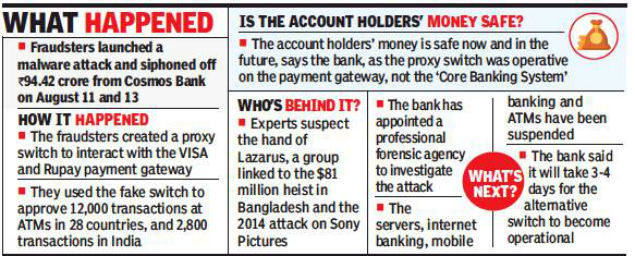
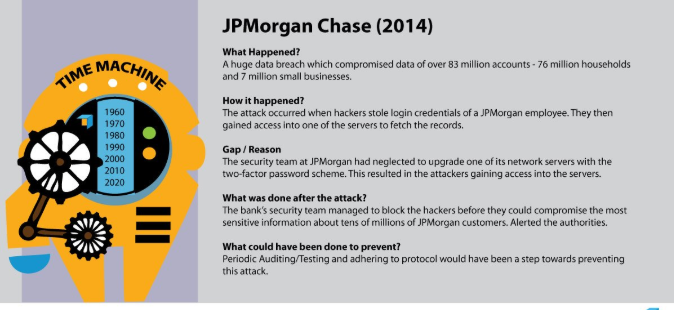
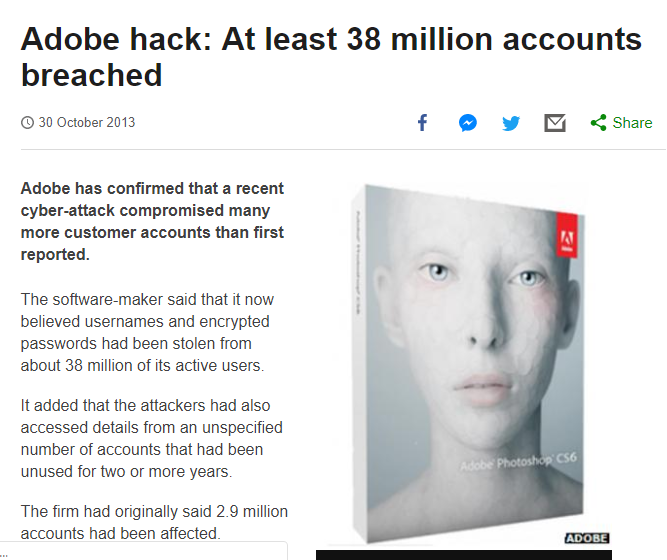
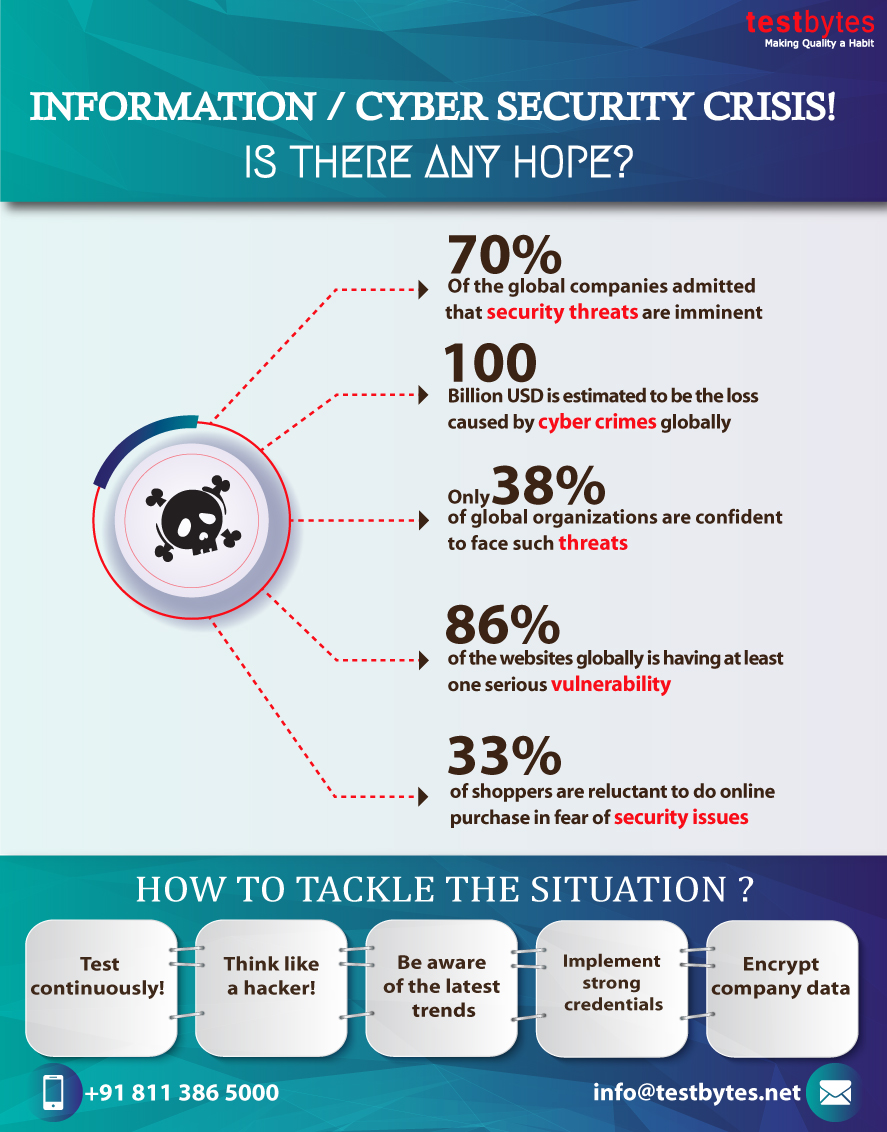
Many of you might be accustomed to HTTP:// or HTTPS://. But what do they mean? What is the Difference Between HTTP and HTTPS?
Let’s have a look at the topic HTTP vs HTTPS in detail.
What is HTTP?
- HTTP stands for Hypertext Transfer Protocol. They are a set of rules which govern the transmission of any information on the World Wide Web.
- HTTP also sets the standard rules for the servers, and web browsers to communicate with each other.
- HTTP, built on top of TCP; is an application layer network protocol.
- HTTP is an application layer protocol. It transfers information between networked devices.
- HTTP works on top layers of the network protocol stack. HTTP flow includes a client machine that sends a request to a server and gets a response message in return.
- HTTP is known as stateless protocol as every command is independent and executes separately. It does not require the reference of any previous command that is executed.
Sample HTTP Request
| GET /index.html HTTP/1.1 Host: www.ABC.com User-Agent: Chrome/5.0 Accept: text/xml,application/xml,application/xhtml+xml,text/html*/* Accept-Language: en-us Accept-Charset: ISO-8859-1,utf-8 Connection: keep-alive <blank line> |
Sample HTTP Response
| HTTP/1.1 200 OK Date: Thu, 24 Jul 2008 17:36:27 GMT Server: Apache-Coyote/1.1 Content-Type: text/html;charset=UTF-8 Content-Length: 1846 <html> … </html> |
Also Read: What does your company cyber system need vulnerability Assessment?
What is HTTPS?
- HTTPS stands for HyperText Transfer Protocol Secure. As the name suggests it’s a more secured and advanced version of HTTP.
- For Data Communication HTTPS uses port no. 443. To enhance the security of all the transactions, HTTPS encrypts all the communications that are done with SSL.
- HTTPS is a mix of HTTP and SSL/TLS protocols.
- HTTPS works by establishing a secure encrypted link between the browser and the server by providing provides two-way security of Data.
- It safeguards your potentially sensitive data from various threats.

Sample HTTPS Request
| request(‘https://example.com/url?a=b’, function (error, response, body) { if (!error && response.statusCode == 200) { console.log(body); } }); |

Features exclusive to HTTPS
HTTPS takes an upper hand on HTTP, and there are a few features that are exclusive to HTTPS. Some of them are:
- GeoLocation: geolocation enables to find the user location and this feature is exclusive to HTTPS only.
- Web push notifications: Web Push notifications are another feature that is exclusive to HTTPS only.
- PWA – Progressive Web App: this very impressive feature allows you to convert your website into an Android mobile app. It is available only on HTTPS.
- GetUserMedia: HTTP puts a limitation on users by not allowing them to use a camera/microphone.
What are the major differences between HTTP and HTTPS?
- HTTP does not have any advanced security mechanism whereas HTTPS offers higher security with SSL or TLS Digital Certificate that provides security to all your communication that takes place between server and browser.
- By default HTTP works on port 80 and HTTPS works on port 443.
- Another major difference lies in that HTTPS runs at Transport Layer whereas HTTP runs at the Application Layer.
- Data in HTTP is transferred as plain text and data in HTTPS is transferred as encrypted text.
- When talking about their speed, HTTP takes a front seat with being faster as HTTPS consumes more time in encryption.
Now let’s talk in terms of the advantages and disadvantages of HTTP and HTTPS.
First, let’s discuss the advantages of both HTTP and HTTPS:
Advantages of HTTP
- HTTP has the advantage of being executed with other protocols on the networks
- It is not dependent on Runtime support
- HTTP pages are faster to access as they are directly stored on computer and internet caches and do not require any encryption.
- It allows cross-platform porting
- It can be used over Firewalls.
- HTTP is platform-independent
- Global applications are possible
- It is not Connection Oriented
Advantages of HTTPS
- Generally, all the sites running on HTTPS, redirect themselves automatically. Even if your type HTTP://, it will be redirected to HTTPS.
- It is used for all secured transactions that allow users like online banking.
- It uses SSL technology to protect users. Each SSL contains unique, authenticated information about the certificate owner.
Disadvantages/limitations of HTTP vs HTTPS
Since we have had a glimpse of the advantages of both HTTP and HTTPS, let’s have a look into their limitations.
Disadvantages of HTTP
- It provides less or no privacy as content is visible to everyone.
- It uses no encryption method and hence the content can be altered by anyone. In short, it provides no security.
Disadvantages of HTTPS
- Though HTTPS provides security, it cannot secure the cached pages on the browser.
- There is no security to the data in the browser memory.
- HTTPS is slower.
- It enhances the computational overhead.
- It increased the network overhead
Difference between HTTP and HTTPS.
| Parameter | HTTP | HTTPS |
| Protocol | It is a hypertext transfer protocol. | It is a hypertext transfer protocol with security. |
| Security | It is less secure. Anyone can read and edit content. | It is more secure and used for secure transactions like banking, etc. |
| Port | Port 80 is the default port | Port 443 is the default port. |
| Usage | HTTP URLs begin with HTTP:// | HTTPS URLs begin with https:// |
| Used in | It is generally used for a website that is focused more on information purposes like blogs | It is used for websites that require security like banking websites. |
| Encryption | It does not encrypt data while transferring it. The information is transferred as it is and hence is more vulnerable to threats | The data is encrypted before being transferred and is again decrypted at the receiver’s end. Since the data is in encrypted form there are fewer chances of any security threats. |
| Protocol | It operates at the TCP/IP level. | Uses HTTP for transmission, with an enhanced TLS/SSL connection for better security |
| Validations | No validations are required | It requires an SSL certificate |
| Data encryption | No encryption | Uses encryption to secure data |
| Search | It does not have any effect on search. It does not play any role in improving search ranking. | It improves the search ranking. |
| Speed | It is faster than HTTPS, as no time is consumed in encryption and decryption | It is slower than HTTP, as time is consumed in encryption and decryption of data |
| Vulnerability | It is very vulnerable to hackers | It is less vulnerable to hackers. |
Also read: Top 10 Vulnerability list released OWASP that can harm your company
What is an SSL Certificate?
Commonly called a TSL, an SSL certificate is a digitally bind-key that contains crucial information about an organization.
After installation of SSL certificates set a padlock that indicates a safe web connection with the PC and the web server connected to it.
SSL certificate helps in encrypting internet traffic and verifies the server identity.
The information included in the SSL certificate
- The domain name for which the certificate was issued for
- For whom was the certificate issued to
- Digital signature of the company
- The authority which issued this certificate
- Issue date
- Subdomains that are associated with the company
- The expiration date of the certificate
- Public key
Why do you need an SSL certificate?
- SSL has the ability to encrypt communication happening between two internet entities so that privacy can be maintained
- SSL ensures that information is sent to the right server. Pretenders who are waiting to exploit can be avoided because of this
- SSL icon is a trust symbol and will drive users to access the website
Types of SSL/TLS certificate used with HTTPS
Let’s look into the different types of SSL/TLS certificates used with HTTPS
- Domain Validation: It validates Domain name ownership.
- Organization Validation: It validates the owner’s identity.
- Extended Validation: It validates Domain name validation, owner identity, and business registration proof.
Things to know before switching from HTTP to HTTPS
There is a mad race for switching from HTTP to HTTPS, and that is for a good. After all, HTTPS offers many benefits over HTTP.
But switching from HTTP TO HTTPS is a tricky task. Though the process might seem simple, it involves a lot of cautionary measures.
There are a few things that you should remember while switching from HTTP to HTTPS.
How to Convert HTTP to HTTPS
- The first step is to get an SSL certificate
- Next, you will have to install it on the website’s hosting account
- In the next step, you have to configure the 301 redirects. To do this you will have to alter the .htaccess file that is seated in the root folder
- The last step is updating the robots.txt file and notifying the search engines about your switch.
This process might seem very easy, but it is not as easy and straightforward as it appears.
You can ease out your work by taking the help of Service providers to configure SSL certificates.
Though it might incur an additional cost, it might save you from a lot of hassle. Also, remember a few things before switching from HTTP to HTTPS:
- Informing the search engines about you switching from HTTP to HTTPS
- For any resources, you can prefer using the relative URLs
- Make sure that your HTTPS site is reachable through robots.txt
- Don’t forget to keep an eye on your site before and after switching from HTTP to HTTPS and keep track of the changes.
SEO Perspective of HTTPS
In recent times, website owners do everything to improve their SEO ranking as it is one of the very important features for any website to remain in the never-ending race to rank higher on search engines.
Websites strive to be listed on the first page of search engines. And one of the tactics to improve the ranking is to switch on to HTTPS, as HTTPS helps in improving SEO ranking whereas HTTP does not.


Why do you need HTTPS for creating AMP pages?
HTTPS is essential for creating AMP (accelerated mobile pages). AMP is truly an innovation by google to load web content as swiftly as possible on mobile devices.
When it comes to baking good rank in SERP and gaining the trust of Google HTTPS plays a pivotal role.
HTTPS serves as an important tanking signal as well as a crucial part of cybersecurity.
How does HTTPS authenticate web servers?
Authentication verifies if a system or person is What they claim to be. HTTP does not support identity verification.
HTTP works on priority rather than security. But with increasing security risks, authentication becomes important.
The private key confirms the server ID like an ID card confirms any person’s ID.
When a user navigates through a website its key is authenticated to ensure that the server is a legitimate host. It prevents a number of attacks like:
- On-path attacks
- DNS hijacking
- BGP hijacking
How to add HTTPS to your website?
SSL is basically a text file with encrypted messages in it.
You can buy it from your hosting service and install it on your server so that communications happen between your server and the entity.
Along with an SSL certificate, you also need to install an intermediate certificate that can help in establishing trust in the SSL certificate by tying it to the authority root certificate
In HTTPS, how does TLS/SSL encrypt HTTP requests and responses?
TLS uses public-key encryption. Via the server’s SSL certificate, the public key is shared with client devices.
When the connection is set between the client and the server, ends uses, private key and public key to reach an agreement with session keys. It is used to encrypt the communication between two devices.
The HTTP requests are encrypted using session keys, making the whole communication secure.
Which one is better when we compare HTTP vs HTTPS?
The answer is clear when it comes to HTTP vs HTTPS.
HTTPS provides added security, it is definitely an added advantage if your website includes some sensitive information as well as in SERP ranking.