Cyber Attacks on India or any other part of this world are an attempt to destroy or infect computer networks in order to extract or extort money or for other malicious intentions such as procuring necessary information.
Cyber attacks alter computer code, data, or logic via malicious code resulting in troublesome consequences that can compromise the information or data of the organizations to make it available to cybercriminals.
A serious threat lurking around, Cyber attacks on India
Around 1.6 million attacks were reported in the year 2020. The world was moving to remote corners of the world and security was under serious threat owing to work from home.
Indian Computer Emergency Response Team (CERT-IN) has alerted over 700 organizations to be alert about cyber attacks and suggested improving their cyber security measures to keep risks at a minimum.
Wish to know which are the Cyber Attacks in India? Read below
Major and Minor cyber attacks on India { Till 2021]
SIM Swap Fraud
In August 2018, two men from Navi Mumbai were arrested for cybercrime. They were involved in fraudulent activities concerning money transfers from the bank accounts of numerous individuals by getting their SIM card information through illegal means.
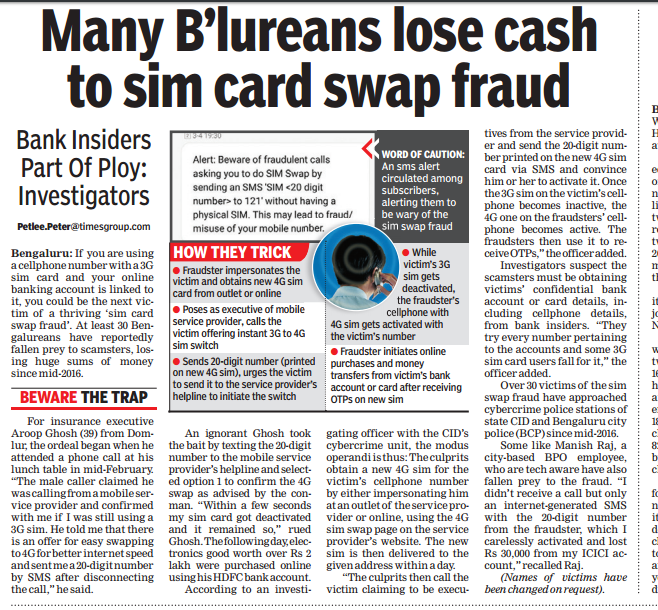
These fraudsters were getting the details of people and were later blocking their SIM Cards with the help of fake documents post which they were carrying out transactions through online banking.
They were accused of transferring 4 crore Indian Rupees effectively from various accounts. They even dared to hack the accounts of a couple of companies.
Prevention: The information required for such a scheme is gathered via various public domains and is misused later. Sharing personal information with unknown applications and domains can help in minimizing the risk of having your personal information reaching people with malicious content.
Fraudsters use the victim’s information in various scams and trick them into fraudulent activities. It is advisable therefore that the site where n individual is entering his banking or other details should be verified for authenticity, as scammer uses the fake site to get the information directly from prospective victims
Cyber Attack on Cosmos Bank
A daring cyber attack was carried in August 2018 on Cosmos Bank’s Pune branch which saw nearly 94 Crores rupees being siphoned off.
Hackers wiped out money and transferred it to a Hong Kong-situated bank by hacking the server of Cosmos Bank. A case was filed by Cosmos bank with Pune cyber cell for the cyber attack. Hackers hacked into the ATM server of the bank and stole the details of many visa and rupee debit card owners.
The attack was not on a centralized banking solution of Cosmos bank. The balances and total accounts statistics remained unchanged and there was no effect on the bank account of holders. The switching system which acts as an interacting module between the payment gateways and the bank’s centralized banking solution was attacked.
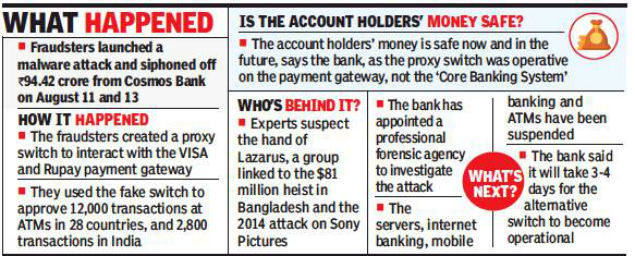
The Malware attack on the switching system raised numerous wrong messages confirming various demands of payment of visa and rupee debit card internationally. The total transactions were 14,000 in numbers with over 450 cards across 28 countries.
Also Know: Cyber Security New Year’s Resolutions For 2020
On the national level, it has been done through 400 cards and the transactions involved were 2,800. This was the first malware attack in India against the switching system which broke the communication between the payment gateway and the bank.
Prevention: Hardening of the security systems by limiting their functions and performance only to authorized people can be the way forward.
Any unauthorized access to the network should immediately set an alarm to block all access to the bank’s network. Also, to minimize risk, enabling a two-factor authentication might help.
Through testing, potential vulnerabilities can be fished out and can make the entire digital part of the banking system safe.
ATM System Hacked in Kolkata
In July 2018 fraudsters hacked into Canara bank ATM servers and wiped off almost 20 lakh rupees from different bank accounts. The number of victims was over 50 and it was believed that they were holding the account details of more than 300 ATM users across India.
The hackers used skimming devices on ATMs to steal the information of debit cardholders and made a minimum transaction of INR 10,000 and a maximum of INR 40,000 per account.
On 5 August 2018, two men were arrested in New Delhi who were working with an international gang that uses skimming activities to extract the details of the bank account.
Prevention: Enhancement of the security features in ATM and ATM monitoring systems can prevent any misuse of data.
Another way to prevent fraudulent activity is to minimize the risk of skimming by using lockbox services to receive and transfer money safely.
This uses an encrypted code that is safer than any other payment.
Websites Hacked: Over 22,000 websites were hacked between the months of April 2017 and January 2018. As per the information presented by the Indian Computer Emergency Response Team, over 493 websites were affected by malware propagation including 114 websites run by the government. The attacks were intended to gather information about the services and details of the users in their network.
Prevention: Using a more secure firewall for networks and servers which can block any unauthorized access from outside the network is perhaps the best idea.
Personal information of individuals is critical for users and cannot be allowed to be taped into by criminals. Thus, monitoring and introducing a proper network including a firewall and security system may help in minimizing the risk of getting hacked.
Phishing Attack on Wipro

There were reports about an attack on the Wipro system by major online news portals. Attack as per reported was a phishing attack and was done by a group through gift card fraud.
Even though the attack was not a massive one, many employees and client accounts were compromised. And the attack became notorious for one of the major Cyber Attacks on India
How to avoid Phishing attacks?
- Always think before you click. Phishing links can impersonate as authentic links with some minor changes that might not be visible at a single glance. Make sure that you have read the complete link before clicking it
- Install measures that can effectively prevent such attacks
- Make sure that the websites you are accessing are secure. Usually, a secure website will have a security certificate to safeguard all the customer information. Make sure that that website begins with HTTPS and has a lock symbol on the extreme left of the address bar.
- Check your online account on a regular basis and make sure that there are no suspicious activities. Change the password frequently.
- Update your browsers regularly as updates often will have security patches for existing loopholes.
- Keep your personal details secret
Bib B Amitabh Bachchan ‘s Twitter Account Hacked!
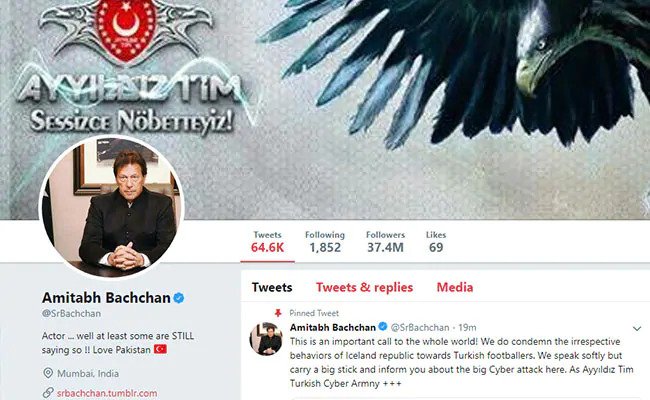
There can be a question that social media profiles are subjected to hacking all the time. But with Amitabh Bachan’s statitude the hack became controversial and was announced as one of the Cyber Attacks on India
Lately, Amitabh Bachchan’s Twitter handle got hacked and the perpetrators posted hateful messages putting everybody in shock.
This can happen to big companies also. However, if the news gets out this can be a huge blow to the credibility of any company.
How to prevent Social Media Profile Hacking?
- Social media is infested with third-party applications. Make sure that you are using legitimate authorized applications
- Use strong credentials and change them often
- Install proper antivirus
- Enable two-factor authentication
Exposed Health Care Data
Be it any government-related data; it has to be kept in utmost secrecy. What if it’s exposed? That’s what happened lately when healthcare data of India was left exposed without enough security measures.
This mistake was found out by Bob Diachenko during a regular security audit. He found out that India based IP contained a data pack that’s been left exposed without any security measures.
How to Prevent Database Hacking?
- Make sure that proper web application firewall is installed
- Strengthen network security by login expiration, changing passwords,
- Make sure that the admin level of your website is not exposed with a simple password
- Change the database prefix from wp6 to something random which can’t be guessed
- Stay updated regarding the latest hacking threats
How to prevent Database Hacking?
- Make sure that a proper web application firewall is installed
- Strengthen network security by login expiration, changing passwords,
- Make sure that the admin level of your website is not exposed with a simple password
- Change the database prefix from wp6 to something random which can’t be guessed
- Stay updated regarding the latest hacking threats
Personal Data Exposed from JustDial Database

An unprotected API end was the issue in this incident. Justdial one of India’s leading local search platforms let a loose end that exposed all of their user data who accessed their services through the web, mobile, and their phone number.
Leaked data includes name, email, number, address gender, etc. the shocking part according to reports is that since 2015 the API has been exposed like this.
How to make your API secure?
- Validate all the incoming data
- Use the essential method for authentication verification
- Monitor and manage using automated scripts
- Encrypt data
UIDAIAdhaar Hacked!
Everyone knows that the Adhaar card is the most important and powerful identification document in India. More than a billion of information stored in the government database is ready to be processed under high security and regulations.
However, in 2018 there was a major flaw that risked the huge data pool. According to reports published by major news portals, a small software patch has actually compromised the data security. There was a threat to national security since Adhaar was emerging to be the most powerful.
Talking about the patch it was an inexpensive one but was capable enough to jeopardize the system security. What made the whole situation frightening was that the Adhaar card was linked to the bank account, pan card, mobile number, and much personal information of an Indian citizen.
However, The Unique Identification Authority of India (UIDAI) who is in charge of the data has denied such allegations. But series of news and proofs that came out might beg to differ.

How to keep sensitive data secure?
- Periodical cybersecurity posture assessment
- Educate the employees on secure network practices
- Adopt a strict BYOD (Bring your own device) policy
- Do heavy encryption on the data that needs to be protected
- Deploy a system that can monitor frequently
SIM Swap Scam
Another big cyber campaign took place in August 2018, when two Hackers from Navi Mumbai transferred 4 crore rupees from multiple bank accounts. They used the SIM Swap system, illegally gaining access to various individuals’ SIM cards and illegally stealing their bank details. They used this private information to get into their bank accounts and transfer their money to their bank account. Hackers blocked individuals’ SIM cards and transacted money through online banking. Not even the individuals tried to hack the details of some of their targeted customers.
Cyberattack on Union Bank of India
Another shocking cyberattack that made everyone alert was done in July 2017. The attack was on one of India’s biggest banks; the Union Bank of India. The attack was initiated when an employee opened an email attachment. This email attachment had a malware code. It allowed the hackers to get inside the bank’s system and steal the bank’s data. The email attachment forged a central bank email. The employee overlooked the details and trusted the email, which initiated a malware attack and allowed the hackers to get inside the bank’s data and steal Union Bank’s access codes for the Society for Worldwide Interbank Financial Telecommunication (SWIFT). SWIFT is used for international transactions. The hacker used these codes and transferred $170 million to a Union Bank account at Citigroup Inc in New York.
Malware attack on Kudankulam Nuclear Power Plant (KKNPP)
Authorities on October 20, 2019, confirmed that the nuclear power station in Kudankulam faced a cyber attack. The attack was initiated by the North Korean hacker group- Lazarus. This attack was done to get information on thorium-based reactors, an alternative to uranium. Initially, National Power Corporation of India (NPCI) denied the hacking attack news but later they accepted that the hackers had hacked one of their systems. They used a malware named ‘Dtrack’ to get inside the company’s system through a couple of loopholes that persisted in their security systems.
Indian journalists, activists spied on by Israeli spyware Pegasus
2019 saw another big cyber attack when Israeli spyware Pegasus was used to spy on academicians, lawyers, activists, and journalists in India.
WhatsApp confirmed that NSO Group used Israeli spyware, called Pegasus to get access to the passwords, text messages on messaging apps like WhatsApp. Pegasus took advantage of loopholes in the servers. It allowed the government spies to hack the details of about 1,400 users. Pegasus allowed to hack and get access to everything on the phones of the user (victims) remotely. Even, WhatsApp announced renovating its security features.
Facebook database leak data of 419 million users
Another very prominent attack was on Facebook and Twitter user data. The personal information of around 419 million users was broken to third parties. The Insecure database allowed the hackers to access the phone numbers, user’s name, gender, and location of around 419 million users that were linked to their Facebook accounts. Though the attack took place around the geographies, it also included the data of many Indian users.
Cyber-attack on Air India
One of the biggest cyber-attacks India has seen in 2021 is on India’s biggest airline Air India. The Security of Indian Airlines data was compromised when the confidential information of its passengers like ticket information, passport details, and credit card information of more than 4.5 million customers was stolen by the hackers. Though the airlines tried to convince their passengers that their credit card information was safe, they insisted they change their password.
LinkedIn Phishing Scam
Another big attack of 2021 was a phishing scam attack on the social networking site LinkedIn. LinkedIn is one of the biggest social networks where people connect with people of their related job profiles. This networking site accounts for 756 million members across 200 countries worldwide. The company was perturbed when the data of 500 million LinkedIn users were under a security breach. The data of these account holders were sold online. The attackers had sent these users fake job offering mail which forced them to click the link and instilling malicious software on their systems.
Attacks on India’s CoWIN app
Amidst the pandemic, CoWIN app emerged as a ray of light for the people of India, by helping them and streamlining the complete vaccination process of the huge country. But this app appeared to be an enticing bait to hackers to lure their victims. Hackers used the CoWin app to misguided users into downloading fake apps. In January many incidents came up in light of fake Aarogya Setu apps created by hackers. It was used to implant malware into end user’s systems. The fake CoWIN app lured many users to download this fake app in an urge to get vaccinated.
Security Testing and its Significance
Hackers and criminals are getting smarter every day. The countermeasure is to predict their attack and block it in the most effective way possible before any unfortunate events.
In Testing, mostly 4 major types of testing ate performed
- Network security
- System software security
- Client-side application security
- Server-side application security
For these tests to happen in the most efficient way possible it’s better to have a dedicated testing wing along with software development or hire services from an agency.
Stopping cyberattacks on India to a full extent might not be possible. But measures can be taken to avoid imminent ones and save a lot of money.