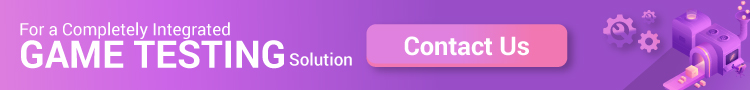
The definition of the term vulnerability assessment from a security perspective is to deeply evaluate, define, classify and prioritize vulnerabilities so that They can be corrected. The process is carried out by vulnerability scanners such as Nikto2, Netsparker, OpenVAS, W3AF, etc.
To know in detail, we have incorporated all the necessary details that you need to know about vulnerability assessment, along with its implementation. So you won’t put your company’s IT system at risk.
Let’s get started!

What Is a Vulnerability Assessment?
An organization’s system consists of various components, such as end-points, applications, and network infrastructures.
All of these provide equal opportunities for hackers to enter into the IT system.
The role of vulnerability assessment here is to check all these elements for vulnerabilities that may be present at any level.
Hence, ensuring proper protection of the system against unauthorized accesses.
A few key points that also get covered under vulnerability assessment are:
- Defining the vulnerabilities
- Identifying the vulnerabilities
- Classification of vulnerabilities
- Prioritization of vulnerabilities
- Laying out knowledge about vulnerabilities
- Providing suitable solutions to the available threats and vulnerabilities
In simple terms, it can also be stated that vulnerability assessments are done in every organization to find and prioritize the available vulnerabilities. This way, the system’s loopholes can be fixed, and all the breaches can be avoided.
These vulnerabilities can be divided into two categories:
- Code Bugs: Sometimes, developers leave bugs/flaws in the code. It becomes a vulnerable point because confidential information can get leaked through it.
- Security Gaps: While all enterprises ensure their system’s complete security, they may leave a gap in their internal processes. It can provide space for intruders to enter their environment and get access to whichever information they want.

5 Crucial Steps in Vulnerability Assessment
- Identify the potential hazards
- Determine the risks
- Evaluate the defense system
- Record the findings
- Periodical review
Top 15 Vulnerability assessment tools
- Netsparker
- OpenVAS
- W3AF
- Arachni
- Acunetix
- Nmap
- OpenSCAP
- GoLismero
- Burp Suite
- Comodo HackerProof
- Intruder
- Retina CS Community
- Crashtest Security
- GamaScan
- Nexpose
Why Is Vulnerability Assessment Crucial?
Vulnerability assessment has now become a vital part of every organization.
It is essential because it provides the enterprises with proper knowledge and understanding of security weaknesses in their environment.
Moreover, the process offers awareness of accessing the present vulnerabilities and the risks associated with them.
Therefore, helping the organizations to avoid any security breaches that can put their business in jeopardy.
Other benefits of vulnerability assessment include:
Defining Risk Levels
Whether you believe it or not, your organization’s security is always under threat.
While this risk is inevitable, you can certainly identify the underlying vulnerabilities with proper assessment. It will help in resolving the dangers and make your system more secure.
Avoid Automated Attacks
Intruders have become smart nowadays. They don’t leave any chance of creating trouble for you. That is why they use automated attacks to check the availability of vulnerabilities in your system and take advantage of it.
Where this makes their work more convenient, it brings more significant risk for your organization. Under vulnerability assessment, experts use the same tools as these hackers. So they can avoid these automated attacks.
Also Read: Best vulnerability assessment tools used for security audit
Prioritizing Risks
Even if you are aware of all the available risks to your organization’s IT system, you may still end up making a mistake. Most people’s standard error here is that they focus more on unnecessary vulnerabilities while leaving behind the significant ones.
But this mistake won’t happen with the help of vulnerability assessment.
The process won’t only identify the threats, but it will also help prioritize them based on their severity.
Therefore, you can ensure that the more significant vulnerabilities get resolved first, and the less severe ones get assessed only after that.
Time And Money Savings
A data breach doesn’t only waste time and money on security restructuring. If your enterprise goes through an attack, you also have to deal with some legal formalities.
Moreover, you will have to invest effort and money in PR to maintain your company’s image.
On the other hand, a vulnerability assessment can easily help you avoid all this hassle by securing the system from known threats.
Hence, you will then be able to focus on more crucial tasks while remaining carefree about the security of your system.

What Are The Types Of Vulnerability Assessment?
Vulnerability assessment is further divided into various types, depending on the area of the IT environment that is being checked. Here are some of the common kinds:
- Network-Based: As the name suggests, this method is opted to find out the vulnerabilities in the organization’s wired and wireless networks.
- Host-Based: This includes a proper examination of network hosts through ports and services. It works on hosts like servers and workstations.
- Web Application: Web applications are an easy point for hackers to enter into the system. This method helps identify the loopholes in the app architecture that can lead to breaches.
- Database: Attacks like SQL injection can lead to severe data losses in an enterprise. Database methods include scanning the entire database for any available vulnerabilities to avoid these attacks.
Other kinds of end-point or network scan can be done to find the risk against any available threats to the organization’s IT system, such as phishing assessment and penetration testing.
Difference between vulnerability assessment and vulnerability management
| Vulnerability assessment | Vulnerability Management |
| Vulnerability assessment has a fixed time period for its occurrence | It’s an ongoing process |
| The process used to find the severity of vulnerabilities | Used to manage Vulnerability assessment or pen testing |
| Performed with the help of automation tools | It’s a collective process |
| Vulnerability assessment is just a part of the cybersecurity program | It’s a detailed process that can handle all the security-related issues |
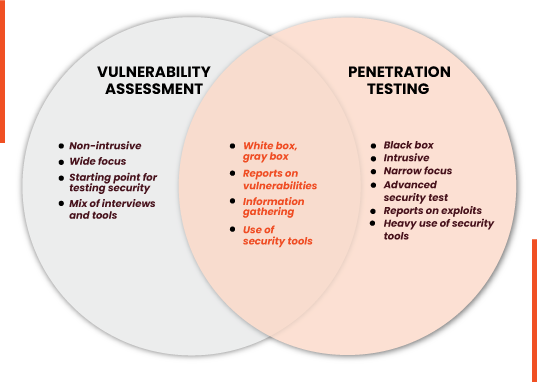
Vulnerability Assessment vs Penetration testing. What’s the difference between vulnerability assessment and penetration testing
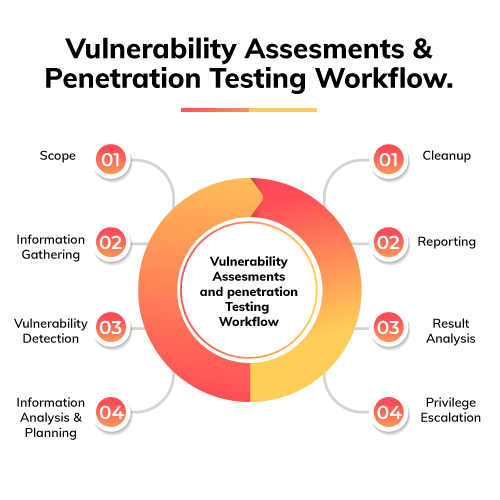
| Vulnerability Assessment | Penetration Testing |
| Used to assess vulnerabilities with the help of a tool that’s capable of doing the scan in an automated fashion | It’s a manual process where each module of software is tested for vulnerabilities individually |
| Usually done through automation | Performed by combining automated as well as the manual process |
| Performed often | Performed once in a year mostly |
| Comprehensive list of vulnerabilities which may include false positives | Serves as a call to action document about vulnerabilities that can be easily exploited |
| Can be performed by in-house security staff | Can only be performed by a third party company who has required resources at the disposal |
Also Read: How much will it cost for penetration testing?
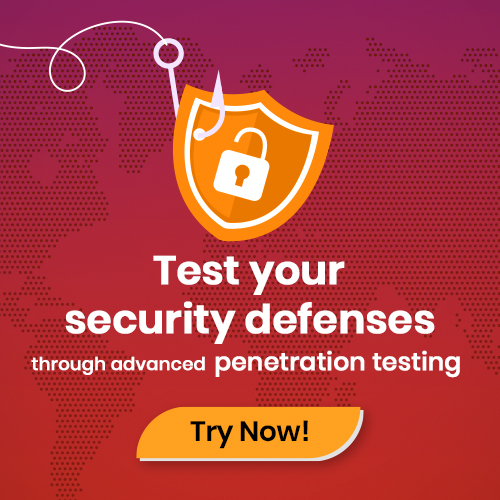
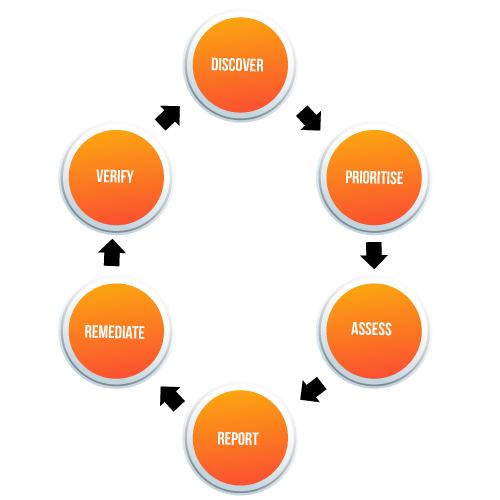
The vulnerability assessment process differs for every enterprise due to its distinct infrastructures.
However, we can still build a basic 5-step procedure that works for most organizations. So it will provide you with an overview of how things get done in this process.
Step 1: Initial Planning
The first step includes proper analysis of the infrastructure to decide all the systems and networks to be checked.
You also need to identify the critical systems and data that have to be protected at any cost.
For example, the databases that hold essential information about your enterprise have to be scanned appropriately.
Remember that each of the professionals working on the process should expect the same output of vulnerability assessment.
It will help in proceeding further suitably. Plus, there should be proper communication throughout the planning so that any errors can be avoided.
Step 2: Scanning
Once you receive a complete list of systems and networks that have to be checked, the next step is to scan them.
Here, you will have to find all the available vulnerabilities in them. The information found on this step won’t be refined.
Therefore, you need not get overwhelmed with the long record of risks and vulnerabilities because several of them can be false positives.
Step 3: Analysis
It isn’t possible to resolve all the received vulnerabilities as some of them can be wrong.
That is why a proper analysis has to be done to find the underlying cause of these vulnerabilities.
Thus, they can get sorted based on their integrity. However, this isn’t the only objective covered in this step.
Along with the viability test, the associated risks, potential impact, and solutions of each vulnerability also get checked here.
After that, the threats are prioritized based on their severity. This helps resolve the more impactful vulnerabilities first and leave the rest for later assessment to cause no significant harm to the enterprise.
A report of the discovered vulnerabilities also gets prepared here, and it includes the following points:
- Vulnerability definition
- Scanning date
- A complete description of the vulnerability
- Common Vulnerabilities and Exposures (CVE) Scores
- Systems and networks affected by the vulnerability, with their details.
- Available remediation techniques for the vulnerability
- Vulnerability PoC (Proof of Concept)
Step 4: Remediation
The ultimate aim of a vulnerability assessment is to eliminate all the available vulnerabilities and make the system secure against the risks.
So if you don’t resolve the found security gaps, there won’t be any use of the previously done steps.
That is why this step includes remediation of the vulnerability found in the earlier procedure.
It can involve a simple code update or a more thorough understanding of what is wrong in the system.
You may need to install new applications, implement the latest security patches, or use other tools for the purpose.
The resolving of vulnerabilities will begin with the high priority vulnerabilities, and then you will have to move to less significant ones.
Experts may recommend leaving some of the no-impact vulnerabilities that aren’t worth the time and effort required to resolve them.
Step 5: Repetition
Vulnerability assessment isn’t a one-time process. Rather, it is a regular activity that must be done under expert guidance to ensure that the organization’s system remains secure from any threat.
That is why the final step here is to create a cycle of this procedure according to your enterprise’s needs.
The importance of a vulnerability assessment increases when you have introduced a new prominent feature, application, or network into the infrastructure.
Therefore, you must make sure that the process gets repeated every once in a while, and the entire IT system remains secure.
And in these five steps, the entire process gets done. You can adjust the steps and include a more thorough study of the vulnerabilities in it based on your enterprise’s requirements.
In case you aren’t sure about something, you can also opt for a service provider.
As they deal with different organizations every day, they will be able to offer you the most reliable solution for your individual needs.
Using Tools For Vulnerability Assessment
Earlier, the process of vulnerability assessment was conducted by the security professionals who knew about the latest threats in the market.
So they conveniently checked the entire IT system against these risks and implemented the required security measures.
This was time-consuming and inefficient, as various unknown threats got left out from the inspection.
Then came the use of automated vulnerability assessment tools. These tools usually opt for the same methods that are used by professional intruders.
Hence, they are able to catch all the vulnerabilities that may give the system’s access to hackers.
The top vulnerability assessment tools include:
- Netsparker
- Intruder
- Aircrack
- OpenVAS
- Nikto
- Microsoft Baseline Security Analyzer
- Acunetix
- AppTrana
- SolarWinds Network Vulnerability Detection
- Nexpose Community
- Tripwire IP360
- Retina CS Community
- Wireshark
- Nessus Professional
- Secunia Personal Software Inspector
How To Choose The Vulnerability Assessment Tools?
Just like it is crucial to conduct a vulnerability assessment, it is also vital to pick the correct tool for the purpose.
Your choice should majorly depend on your enterprise’s requirements. The factors that you must consider before opting for a specific vulnerability assessment tool are:
Compatibility
The first aspect you need to check in your chosen tool is whether or not it is compatible with your organization’s systems and networks.
In case it misses out on even one of these components, it will be of no use for you.
Only a compatible tool will be able to provide you with accurate information on the available vulnerabilities, prioritization, and remediation.
Therefore, you must ensure that your selected product fulfills all the requirements.
Testing Repetition
The final step of a vulnerability assessment is to repeat the process in a pre-determined duration to make certain that the overall system remains secure at any point in time.
Now, the tool you pick for this purpose depends on the intervals you choose for vulnerability assessment.
Usually, this factor can be categorized into two types:
- Continuous: These tools work round the clock. Thus, you need not worry about the security aspect anytime, as the tool will take care of that. It is mostly preferred in places where the risks of data breaches are exceptionally high.
- Intermittent: Another category of tools are the ones that work on some intervals. While it ensures proper security, it won’t check the systems round the clock. Most organizations prefer this type of tool, as it provides them with the desired results without much hassle.
You can pick either of them based on how much your enterprise is under risk of security breaches.
Cloud Support
Clouds have become a crucial part of every organization because they are easy to maintain, provide access from any point, and don’t cost much.
Along with their extensive benefits, these cloud platforms can also become a bane for your enterprise if you don’t ensure its security.
That is why your chosen vulnerability assessment tool should support the scanning of cloud-based platforms.
Remember to opt for this feature even if you don’t use any clouds currently.
This way, you won’t have to worry about switching your vulnerability assessment tool whenever you decide to move to cloud platforms.
Update Quality and Speed
Quality and speed are the two most essential factors in the modern world. They make certain that the delivered product or service is reliable and efficient.
That is why they need to be checked in your vulnerability assessment tool as well.
The vendor must provide quality updates within the best possible time. For example, the time gap between a new threat being discovered and the vendor updating the tool for detecting the same should be as small as possible.
Prioritization
Prioritization is the most crucial step of the entire vulnerability assessment process.
This step alone makes sure that more significant threats get handled first so that no complication occurs later.
That is why you need to check the selected tool’s prioritization procedure.
Every vulnerability assessment tool uses an algorithm to prioritize the detected vulnerabilities.
Depending on the vendor, various factors may be incorporated into this algorithm to produce a more refined priority list of risks.
You have to go through these aspects and ensure they work properly according to your enterprise requirements.
Industry Standards
The tool selected by you must obey all the industry standards in which your enterprise works. For example, the pharma sector requires vulnerability checks for its supply chain and mobile workforce.
On the other hand, the banking industry needs to ensure that their systems are updated and secured. So whichever domain you work in, the tool should fulfill its basic requirements and standards.
By checking all these essential factors, you will make certain that your chosen vulnerability assessment tool doesn’t fall short in any aspect. Hence, it will provide you with the best results.
Conclusion
No matter how secure and protected you keep your enterprise’s environment, intruders always find a way to get through the layers.
You can still ensure that your system’s weak points don’t create a more severe problem. For this, you can opt for a vulnerability assessment.


 .
.