Increasing usage of internet has also led to an increase in cyber-crimes / cyber-attacks. But how many types of cyber-attacks are you familiar with? In order to tackle cyber threats, you must be well aware of its nature. So here are the top 10 types of cyber attacks that you need to know about.
What are Cyber Attacks?
A Cyber Attack is defined as an attack originated by a digital system against another digital device, website, or any other digital system and compromises its privacy, reliability or the data stored in it.
Not only these attacks are a threat to digital individuals but are a great threat to businesses as well.
“The total volume of cyber-attacks has increased almost fourfold between January 2016 and October 2017.” – Cisco Annual Cyber-security Report
Why are Cyber-Attacks Initiated?
Before moving further to types of cyber-attacks, let us first have a look at the reasons for initiating cyber-attacks:
- Acquiring unauthorized access to a digital network, system or its data.
- Denial of service
- Virus or malware installation
- Hacking a website for unsolicited purposes
- To get access to personal and secure information of people and businesses
- Unauthorized use of a computer
Types of Cyber Attacks
Cyber-attacks can be of various types. You need to be aware of all those types of cyber attacks to guarantee your utmost safety and security.
1) Malware
Malware is considered as software that is intentionally developed to disrupt computer, server, client, or computer network.
Malware can be in the form of scripts, executable codes, active content, and other malicious software.
These codes can be computer worms, viruses, ransomware, Trojan horses, adware, spyware, or scare ware. Malware, as the name suggests, is designed with a malicious intent to cause damage to the website/computer user.
The most prominent damages caused by malware are:
- As ransomware, it blocks access to key components of the network.
- Installs harmful software/malware
- As spyware, they can steal valuable information from your system (spyware)
- They can damage certain hardware components of your system and make them inoperable.
2) Phishing
The main aim of Phishing is to steal restricted and private information such as credit card details, login ids, and passwords, etc.
By impersonating oneself as a reliable establishment in electronic communication. It is usually done through email spoofing or instant messaging.

They carry a link that directs users to a fake website which looks similar to the legitimate site and asks them to enter personal and secure information. It is a fraudulent activity intended to cheat users.
They bait the users by claiming to be from a reliable third group such as auction sites, online payment processors, social web sites, banks, or IT administrators.
You need to be well aware and acknowledged with such fraudulent activities to bypass any such fraud activities.
3) Man-In-The-Middle Attack
In Man-in-the-middle (MitM) the invader covertly modifies the chats and dialogues between two people who are communicating with each other.
In a Man-in-the-middle attack, the communicators are made to believe that they are directly communicating with each other without any interference from any third party.
But the truth is that the whole communication is controlled by the invader while making the communicators believe that they are talking to each other. It is also known as eavesdropping.
The Entry Points For MITM
- The invaders can easily take control of o private chats over an unsecured public Wi-Fi. Invaders can inset between the device and the network and can take control of the private hats in the network. The communicators without having any idea pass all the conversation to the invaders.
- It can also be done through malware. In such cases, the invader installs software on the victim’s device to process all his information.
4) Denial-of-service attack
In denial-of-service attack (DoS attack) the offender tries to make digital assets inaccessible to its anticipated users.
The offender provisionally interrupts services of a host who is linked to the Internet. It involves overflowing the besieged machine with surplus applications to burden it from fulfilling the legitimate requests.
5) SQL Injection attack
A Structured Query Language (SQL) injection attack allows the intruders to run malicious SQL statements. These SQL statements have the power to take over the database server.
Using SQL injection intruders can overcome application security measures.
It allows them to pass through the validation and approval process of any web application.
It also allows them to recover the entire data from their database. It also gives access to intruders to add, modify, and delete data in the database.
An SQL Injection allows intruders to fiddle with various databases including MySQL, Oracle, SQL Server, or others. It is widely used by attackers to get access over:
- Personal data
- Intellectual property
- Customer information
- Trade secrets and more.
6.Zero-Day Attack
The zero-day vulnerability is a defect in the software, hardware or even the firmware.
It is hidden from the teams responsible for fixing this bug. It is referred to as zero-day as it has a zero day time gap between the time it is detected and the first attack.
7. Cross-Site Scripting
In Cross-Site Scripting (XSS) attacks the malicious scripts are embedded to reliable websites.
The intruders send malicious code to different users by embedding them into a trusted website usually as a browser side script.
The web browser cannot recognize this malicious script and has no idea that it is unreliable, and hence it executes the script as it comes from a trusted source. But alas these malicious scripts have powers to access any session tokens, cookies, or any other secret information that is used by that site.
8. Credential Reuse Attack
With almost every personal account asking for Ids and passwords, we tend to reuse them for various accounts.
Though it is a big NO, we tend to reuse one id and password for many accounts. Reusing the same password can be a big threat to your security.
The intruders can steal your usernames and passwords from a hacked website and they get a chance to log in to your other account using the same id n passwords.
And if you have reused them they get a golden opportunity to peek into your private accounts including your bank account, email, your social media accounts, and many others.
And we really do not need to tell you how hazardous it could be! So follow password security best practices and avoid using the same id and password for multiple accounts. You can use Password managers to manage the various IDs you use.
9. Password Attack
Passwords are the main gateways to securely enter into your personal accounts. Getting access to these passwords is an age-old and most convenient way to intrude into someone’s private account.
Our passwords are usually connected to our life’s incidents, people and places and hackers take benefit of such details. They can even sniff into the network to gain access to unencrypted passwords.
Attackers can use either of the below given two approaches to get hack your passwords:
- Brute-force
Brute force is just like any other guessing game where you apply your wits and logic and expect that one of your guesses might work.
- Dictionary attack
In such attacks, attackers use a dictionary of common passwords to intrude into the user’s computer and network.
The attackers copy encrypted file having the list of passwords, and use it to a dictionary of frequently used passwords. They then compare the results to take hold of the user’s password.
The account lockout policy is the best method to evade such risks as it locks your account after a few wrong attempts and hence securing your accounts.
10) Drive-By Download Attack
Drive-by –download attack is a common method used by hackers to spread malicious scripts or codes on user’s systems.
Attackers embed a malicious script into an insecure website’s pages. Whenever you visit such websites, the scripts will automatically install on your system or might redirect you to a website that is controlled by the attacker.
These attacks can occur by visiting a website, a pop-up window or an email message. Drive-by downloads do not require users input to get activated.
It does not require you to download/open any malicious attachment. It uses an operating system/ web browser with inadequate security features.
To avoid the risk of drive-by download attack you should:
- Keep operating systems and browsers up to date
- Avoid suspicious websites.
- Try to use known websites as much as possible.
- Don’t download unnecessary programs and apps.
- Keep minimal plug-ins.
10 Major Cyber-Attacks of 21st Century
Now when we have learned about various types of cyber-attacks and we are sure about their ugly existence. Cyber-attack can happen to any digital user at any time and at any place.
Some might be harmless or might cause just a little damage. But there are a few types of cyber attacks that had caused significant damage and had taken entry in the list of most significant cyber-attacks.
And Here are 10 Major Cyber-Attacks on 21st Century..
1. Cyber-Attack on Yahoo!

One of the most prominent internet giant, Yahoo suffered a big blow when the security of their 3 billion user accounts was put on stake.
The names, dates of birth, email addresses, passwords as well as security questions and answers of 3 billion users were put on stake. The attack took place in 2013-2014.
The attack had severely affected the company; the Yahoo group that was once valued at $100 billion was finally sold off to Verizon for only $4.48 billion for its core Internet business.
The name of the company was later changed to Altaba, Inc. after the sale.
2. eBay Cyber-Attack
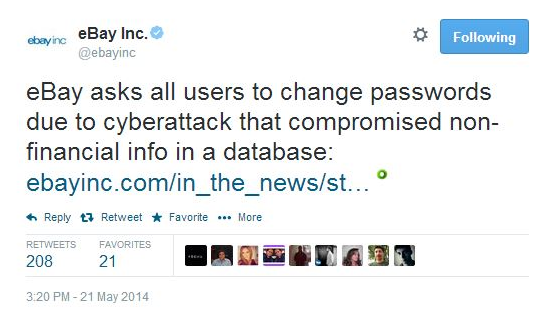
Another cyber-attack that shook the entire world was the user’s database hacking by the intruders.
The e-commerce giant was subjected to a major cyber-attack in May 2014 when hackers intruded into the user’s database using their corporate employee’s accounts.
The hackers had complete access into their network for about 229 days. The breach compromised the sensitive information like names, dates of birth, addresses, and encrypted passwords of around 145 million users.
But as per the company, the financial data of the customers was safe at it was stored in a separate database and was not compromised. The beach resulted in widespread criticism of the company and incurred great loses.
Recommended Read: Major Cyber Attacks on India (Alarming News)
3. Equifax Cyber Attack
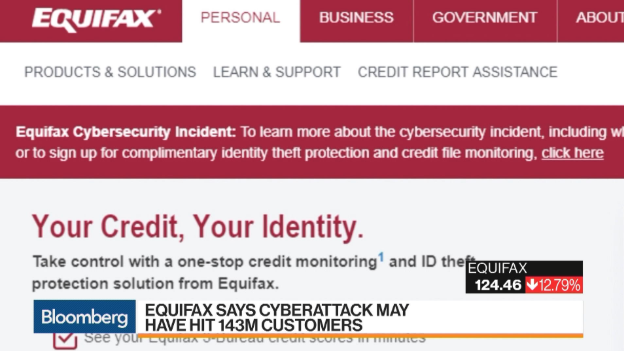
Equifax one of the US largest credit bureaus, faced a major blow when the data of its 143 million costumers was hacked.
The customer’s sensitive information including birth dates, Social Security Numbers, addresses, and drivers’ license numbers was hacked by the intruders.
The attack did not end with hacking only the personal information, even the credit card information of around 209,000 consumers was stolen too.
According to the company, the application vulnerability on their site resulted in the data attack. The attack was exposed on July 29, 2017, but was suspected to have started in mid-May the same year.
4. Target Stores Data Breach

End of December 2013 gave a big blow to Target stores when they discovered that a data breach into their system had compromised the Credit/debit card details and/or contact information of around 110 million people.
The hackers penetrated into their private network by exploiting their vulnerability through a third-party vender for HVAC system to POS payment card readers. The cyber-attack cost them around $162 million.
Know about : What is Data Breach? How to Prevent Data Breach
The CEO and CIO of the company had to resign after this major cyber-security issue.
5. Uber Cyber-Security Breach
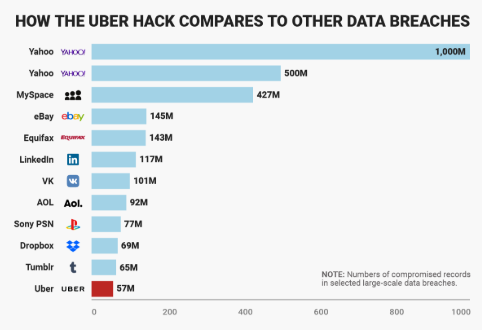
Data breaches are common events in the current digital world. How the companies deal with it, also play an equally important role. Uber was subjected to a data breach in late 2016. The company was not much criticized as its take on this attack was.
The breach resulted in compromising names, mobile phone numbers and email addresses of 57 million Uber users and 600,000 Uber driver’s driver license numbers.
The company discovered of the breach in late 2016 but made it public almost after a year. Not only that the company offered the hackers an amount of massive $100,000 to destroy the data without verifying they actually did.
The breach had resulted in the loss of both the reputation and finances of the company. The company was in negotiation to sell its stakes to Softbank, at the time the breach was announced. The breach lowered the value of the deal from $68 billion to $48 billion.
6. JP Morgan Chase Data Breach
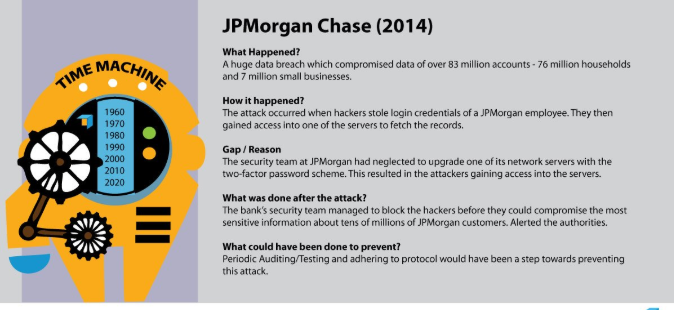
JP Morgan; one of the finest bank of the USA suffered from a cyber-attack which compromised the contact information – names, addresses, phone numbers and email addresses of 6 million households and 7 million small businesses.
There were no monetary losses. The hackers gained privilege over 90 bank servers. July of 2014 would really have been tough for JP Morgan to have a deal with all such critical issues.
7. US Office of Personnel Management – The OPM Data Breach

USA was taken off when the Chinese hacker intruded into their OPM through a third-party contractor.
The attack started in 2012 but was discovered only on March 20, 2014. A second hacker again hacked into their OPM system in May 2014 but was discovered only after almost a year.
The attackers hacked the sensitive information including security clearance data and fingerprint information of over 22 million current and past federal workers.
8. Cyber Attack on Sony PlayStation Network
One of the biggest data breaches in the gaming industry of all times happened on the Sony PlayStation Network. April 20, 2011, is a date that will always be remembered in the gaming industry for the biggest data breach in the gaming industry.
The hackers hacked 77 million Network accounts. These accounts had 12 million accounts that had unencrypted credit card numbers.
The hackers hacked full names, e-mails, credit card numbers, passwords, purchase history, PSN/Qriocity logins and passwords, and home addresses.
Sony incurred losses of an estimate of $171 million. It resulted in an initial $15 million reimbursement in a lawsuit over the breach.
9. RSA Security Attack

March 2011, is a date that is still in debates for the cyber-security breach of the mighty security giant’s SecurID authentication tokens of the company RSA.
The hackers successfully managed to perform phishing attack on RSA employees and impersonated as individuals and intruded into the network of the company. The attack is estimated to have stolen 40 million employee records.
10. Adobe Cyber Attack
Another big cyber-attack that shook the IT giant Adobe happened in October 2013.
The attack compromised the personal information including customer names, IDs, passwords and debit and credit card information of over 38 million users.
The company paid $1 million as legal fees to resolve prerogatives of violating the Customer Records Act and biased business practices.
When market biggies like Yahoo, eBay, Equifax, etc. can get trapped in the trap of cyber-attacks, you too can! So be aware and follow all cyber-security safety measures religiously and BE SAFE!
Response on Cyber Attack
Even after taking precautions cyber-attacks can knock your digital doors. In such cases your initial responses should be:
- It the attack real or just a prank
- If you can access your data; take a backup.
- If required approach legal authorities
- If employees misuse their rights take appropriate actions
- If services are denied, the website traffic should be diverted to other servers.
Prevention of Cyber Attacks
Though there is no guarantee to debar cyber-attacks completely, you can take as many precautions as you can to avoid them. Some of the steps you can follow to safeguard you are:
- Use a good anti-virus that can detect various malware and can stop them from getting inside your system.
- Use a good firewall. Use a good quality third party firewall apart from your default firewall.
- In a corporate computer network, assure that no Plug and Play is supported in any system.
- Corporates should use good network traffic analyzer to track any strange usage behavior from any system.
- To protect yourself from DDoS attacks, mitigate your website to different servers and even better to use cloud service.
- To prevent high-grade attacks seeks the expertise of a security testing company. Their vulnerability assessment report will be extensive and will tighten all the loose ends of the digital products and windows of your company.
Conclusion
Cyber-attacks are a sad reality of the digital world. Proper legislative rules are now laid down to protect the users from these hazardous attacks. Cyber-attacks are much more than just gaining unauthorized access to other’s systems.

They can be very hazardous. And can lead to loss of money, brand name and can even be a big blow to your integrity. So being a digital user, it is just for you to know about all these types of cyber attacks and take proper measures to avoid them and take proper steps in case you are fallen a victim to them.
