Online applications are becoming increasingly refined as the world gets more organized.
Small and mid-sized organizations currently depend aggressively on web applications for maintaining their business and expanding income.
Application engineers, designers, and developers are currently centered around making more secure application structures and on planning and composing secure code.
With the end goal to make an application safe, it is basic to have a solid procedure for security testing.
What’s exactly Information Security Testing?
Information security testing is the act of testing stages, administrations, frameworks, applications, gadgets and procedures for data security vulnerabilities.
It is regularly exceptionally robotized with instruments that examine for known vulnerabilities and mimic assaults utilizing realized risk designs.
It might likewise incorporate a progression of manual risks by talented data security pros.
How do you start with Information Security Testing?
Installing security testing in the improvement procedure is basic for uncovering application layer security flaws.
Subsequently, security testing must begin ideally from the necessity gathering stage to comprehend the security prerequisites of the application.
The ultimate objective of security testing is to recognize whether an application is powerless against risks, if the data framework ensures the information while looking after usefulness, any capability of data spillage, and to survey how the application acts when looked with a destructive attack.
Security testing is likewise a part of practical testing since there are some fundamental security tests that are a piece of functional testing.
Also Read : The Security Challenge Posed by the Internet of Things: How to Rectify Them
Additionally, security testing should be organized and implemented independently. Not at all like functional testing that approves what the analyzers know and ought to be valid, security testing centers around the unclear components and test the endless ways that application would be able to.
Types of Security Testing:
In order to come up with a safe application, security analyzers need to direct the accompanying tests:
Vulnerability Checks:
Vulnerability check tests the whole framework under test, to recognize framework vulnerabilities, escape clauses, and suspicious powerless marks.
This sweep recognizes and characterizes the framework shortcomings and furthermore predicts the adequacy of the countermeasures that have been taken.
Infiltration Testing:
An infiltration test additionally called a pen test, is a recreated test that copies an attack by a programmer on the framework that is being tried.
This test involves gathering data about the framework and recognizing passage focuses on the application and endeavoring a break-in to decide the security shortcoming of the application.
This test resembles a ‘white hat attack’. The testing focuses on testing where the IT group and the security analyzers cooperate, outer testing that tests the remotely noticeable passage focuses, for example, servers, gadgets, space names and so on.
Inside testing, that is led behind a firewall by an approved client, checks how the application acts in case of a genuine attack.
Security Risk Assessment:
This testing includes the appraisal of the danger of the security framework by exploring and breaking down potential dangers.

These dangers are then ordered into high, medium and low classifications dependent on their seriousness level.
Characterizing the correct alleviation systems dependent on the security stance of the application at that point pursues.
Security reviews to check for administration passageways, between the system, and intra-arrange access, and information assurance is directed at this level.
Moral Hacking:
Moral hacking utilizes an ordered authority to enter the framework imitating the way of genuine programmers.
The application is attacked from inside to uncover security defects and vulnerabilities and to recognize potential dangers that pernicious programmers may exploit.
Security Scanning:
To upgrade the extent of security testing, analyzers should direct security outputs to assess arrange shortcoming.
Each sweep sends malignant solicitations to the framework and analyzers must check for conduct that could show a security weakness.
SQL Injection, XPath Injection, XML Bomb, Malicious Attachment, Invalid Types, Malformed XML, Cross Site Scripting and so forth are a portion of the outputs that should be rushed to check for vulnerabilities which are then learned finally, broke down and afterward settled.
Access Control Testing:
Access Control testing guarantees that the application under testing must be gotten to by the approved and authentic clients.
The goal of this test is to survey the separating strategy of the product parts and guarantee that the application execution adjusts to the security arrangements and shields the framework from unapproved clients.
Why is Information Security Testing Important?
A complete security testing structure manages approval over all layers of an application.
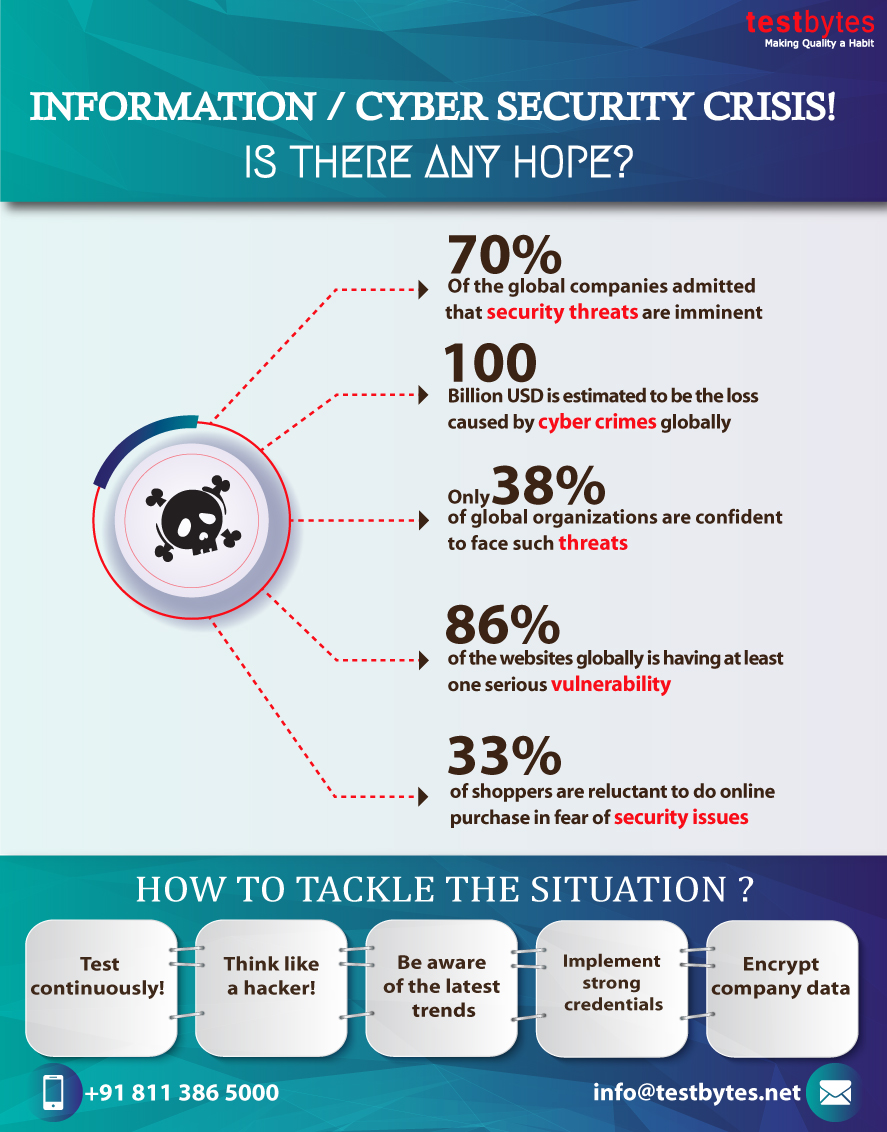
Beginning with examination and assessment of the security of the application, it moves additionally covering the system, database and application presentation layers.
While application and mobile testing serve to assess security at these levels, cloud penetration testing uncovers the security chunks, when the application is facilitated in the cloud.
These testing ideas make utilization of a mix of automated scanner instruments that assess lines of code for security irregularities and infiltration testing that reenacts attacks by unintended access channels.
Defenselessness appraisal shapes a critical part of security testing. Through this, the organization can assess their application code for vulnerabilities and take therapeutic measures for the equivalent.
As of late, a significant number of the product improvement enterprises have been making utilization of secure software development lifecycle procedures to guarantee recognizable proof and correction of vulnerable areas at an early stage in the application improvement process.
How does Security Testing increase the value of Organizations?
In the present interconnected world with buyers depending even more on online channels to make exchanges, any security threats, however major or minor it might be, prompts misfortune in client certainty and at last income.
Further, the security threats have additionally developed exponentially, both in quality and in addition to affecting potential prospects.
In such a situation, information security testing plays the main role that enables an association to recognize where they are defenseless and take the restorative measures to repair the holes in security.
An ever increasing number of enterprises are completing the security reviews and testing measures with the end goal to guarantee that their central goal i.e. basic applications are protected from any breaks or unintended entrance.
The broader an organizations security trying methodologies are, the better are its odds of prevailing in a progressively menacing innovation terrain.
Information safety efforts empower an organization to dodge the traps emerging from accidental leakage of delicate information.
Ordinarily, such spillages cost them beyond a reasonable doubt, by virtue of legal difficulties emerging because of affectability of data.
Information safety efforts diminish the consistency cost by improving information review components and automating them.
They additionally empower the organization to guarantee respectability of information by avoiding unapproved use and alterations.
In the present, very much associated world, appropriation of information security procedures and systems guarantee that the association is all adjusted to the legitimate and consistence norms across nations.




