Regardless of whether your New Year’s goals incorporate well being related objectives, the way of life changes, or different responsibilities, there’s one territory we as a whole should concentrate on in 2020: that’s cybersecurity. There have to be Cybersecurity New Years resolutions for better cyberspace.
In view of far-reaching appraisals of the danger scene, we suggest that organizations center around the accompanying security points in 2020:
Before that, you must go through some of the major attacks that happened last year to get a clear picture of the necessity of the implementation of strict procedures.
Why you need Cybersecurity New Years resolutions?
The answer is, Worst attacks that happened in 2019!
• Capital one was hacked and around 100 million customer data was stolen
• State Farm an insurance company has revealed that they were under attack lately
• Thousands of Disney fans accounts were hacked once they logged onto a new streaming service
• A cryptocurrency exchange was ransacked in South Korea and $48. Million was stolen
• 1 Million user data of BioStar 2 was stolen
• More than half a million data of DHS Target was exposed through a phishing attack
• There is a suspicion that data breach has happened in Citrix
1. Practices to avoid Crime-As-A-Service (CaaS)
Crime-As-A-Service (CaaS) is the point at which an expert criminal, or group of culprits, create a prompt gadget, “instruments” and other bundled administrations, which are then made available to be purchased or leased to different criminals who are typically less experienced.
This is powerfully affecting the universe of wrongdoing – and cybercrime specifically – in light of the fact that it brings down the bar for unpracticed on-screen characters to dispatch advanced digital assaults and tricks.
In 2017, Europol discharged another investigation that hailed CaaS as a noteworthy facilitator of genuine online crimes, and additionally customary violations like unlawful weapons deals.
Crime-As-A-Service will build the dangers of money related misrepresentation; digital blackmail and information robbery for a wide range of organizations, yet small and medium-sized organizations are at the most serious hazard.
Hence, it is basic for entrepreneurs to make a “safeguard top to bottom” approach that centers similarly to preventive security and post-attack regulation. By preparing for a system theft, the organization can limit the harm.
2. Expand Tools and Services
Digital security dangers are expanding in seriousness and recurrence, which is stressing the IT-associations in numerous organizations.
To help these organizations in their voyage to better digital security, many tools have extended their administrations portfolio with down to earth digital security administrations.
The administrations incorporate Cybersecurity well-being check for evaluating the present condition of the digital security in the organization, incident reaction for handling a progressing cyber attack and Defense working for enhancing the digital security on the functional side.
Moreover, IT-bolster as an administration is offered to give persistent help.
3. Controlling the menace of the Internet of Things (IoT)
By interfacing a more noteworthy decent variety of gadgets to systems, this carries with it the related dangers. To place this into viewpoint, there are in excess of three billion cell phones right now being used universally and eight billion IoT gadgets.
The scale is considerable and it is just developing. The Gartner report predicts more than 20 billion associated things by 2020, all of which speak to entry to the system, which can be hacked or traded off.
Read also : Top 10 Most Common Types of Cyber Attacks
To secure associations against this multiplying hazard isn’t simple, however, should be possible. The security of every hub in the system is important to bestow security all in all.
Endpoint approval is essential to security, as is controlled system associations. For instance, a representative associating his Fitbit to the work PC can result in an unintended trade-off of the system.
4. Risk management in the supply chain
Supply chains are an essential segment of each association’s worldwide business tasks and the foundation of the present worldwide economy.

Be that as it may, security managers are worried about the fact that they are so open to a wealth of hazard factors. A scope of significant and touchy data is frequently imparted to providers and, when that data is shared, coordinate control is lost.
This prompts an expanded danger of its secrecy, uprightness or accessibility being imperiled. In the coming year, associations must concentrate on the weakest spots in their supply chains.
Few out of every odd security trade-off can be anticipated, yet being proactive currently implies that you—and your providers—will be better ready to respond rapidly and insightfully when something happens.
Read also : What is a DDoS attack? How to Stop DDoS Attacks?
To address data change in the inventory network, associations ought to embrace solid, adaptable and repeatable procedures — acquiring affirmation proportionate to the hazard confronted.
Store network data chance administration ought to be installed inside the existing acquisition and the executive’s forms.
This status may decide aggressiveness, monetary well-being, share the cost, or even business survival in the consequence of a break.
5. Embrace the Cloud Storage Services
Distributed storage administrations are extremely popular now and for valid justifications. The best of them offer end-to-end encryption of your information to guard it, alongside some free storage room and sensible expenses for extra space.
Cloud storage services are available and easily retrievable by PCs and mobile phones wherever you are.
There are a lot of other distributed storage administrations—mega backup, Next cloud, Box, Spideroak One, and iDrive, to give some examples. Avoid administrations that are new.
You wouldn’t have any desire to sign on one day and discover that the startup you use to store your information has left the business.
6. Enable multi-factor authentication
To avoid identity theft and other malpractices it’s always better to confirm the user’s identity to add that extra layer of protection. Usually, it’s done by either through the mobile number or email ID of the user. Last year, the poor authentication process leads to a loss in millions. So obviously user authentication has to be done.
7. Block suspicious websites
Clear guidelines must be given to employees not to access any unknown website. Apart from the necessary, other websites must be blocked. Those who are not aware of how to distinguish a malicious site from a good one must be taught immediately.
8. Make sure that the board of directors and CISO are in one page:
Unrealistic goals are the main villains when it comes to attaining effective cyber threat protection for many companies. People at the top are not aware of the fact that fully secure cyberspace is a myth for any company.
What has to be done here is with the help of technology effective strategies must be devised to make sure that nothing happens. To make it happen, time is necessary and both CISO (Chief Information Security Officer) should have a proper idea about the strategies, technologies and time required.
9. Regular update of technologies
When it comes to cybersecurity, software plays a major share in protecting user data or saving any company from cyber-attacks. Bots, viruses, and attacks are evolving as we speak. So regular updates of the technologies used in protecting your company must also be updated regularly.
10. User strict filer for emails
Spam mails are a regular thing for anyone who is using corporate email. A major share of them is advertisement but certain e-mails can breach the spam filter and reach you as a potential lead or an important mail. Once you click it, its true color will be revealed. Jeopardizing company data is a big no under any circumstances so make sure that strict filters are used in every computer in your company.
Conclusion
Regardless of what’s on your New Year’s goals list, cybersecurity is basic at present. Occurrences will happen as it is difficult to stay away from each breach.

However, you can focus on building a developed, practical, expansive based, and community-oriented way to deal with digital security and flexibility.
Developing your organization’s capacity to identify interruptions rapidly and react speedily will be of the most noteworthy significance in 2020 and the upcoming future.












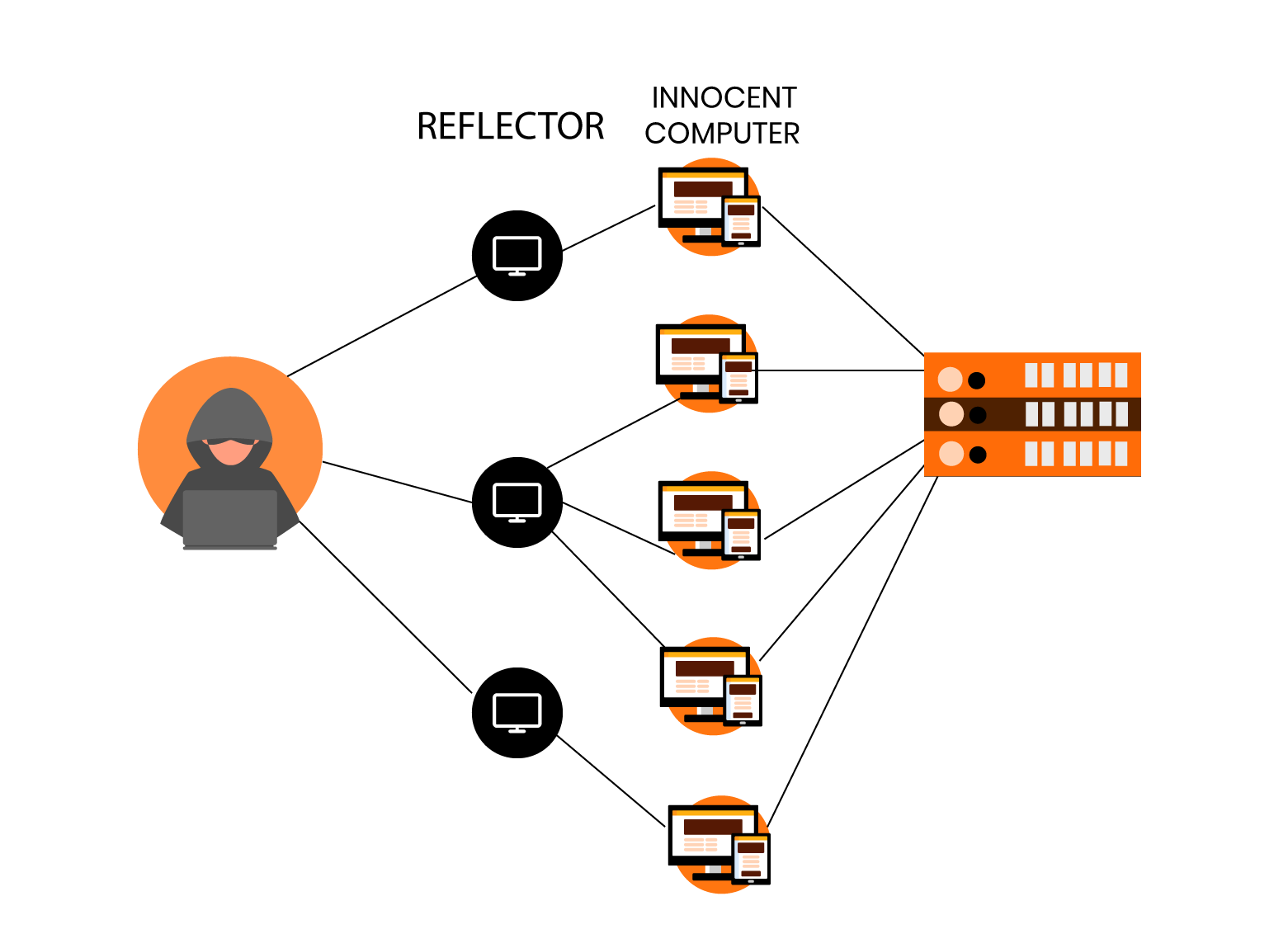
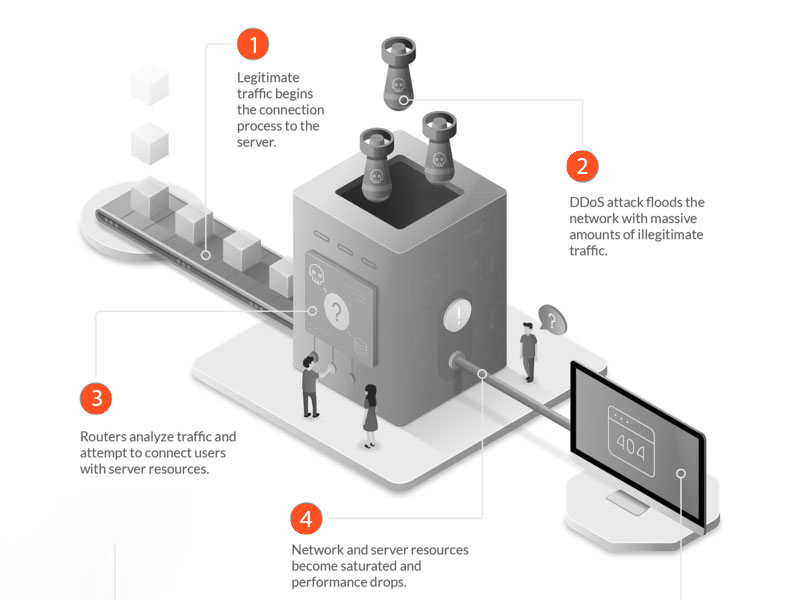
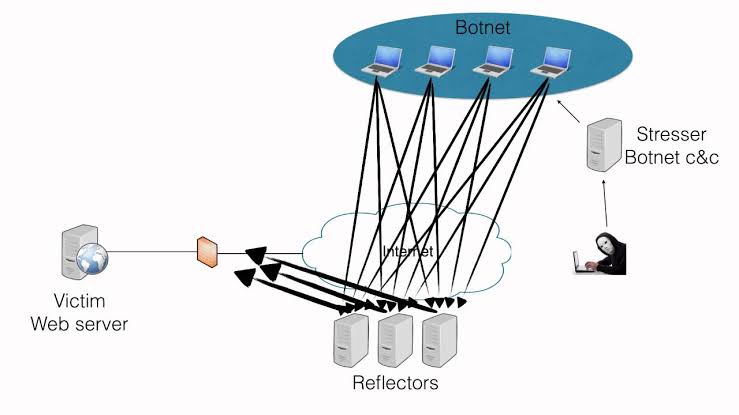
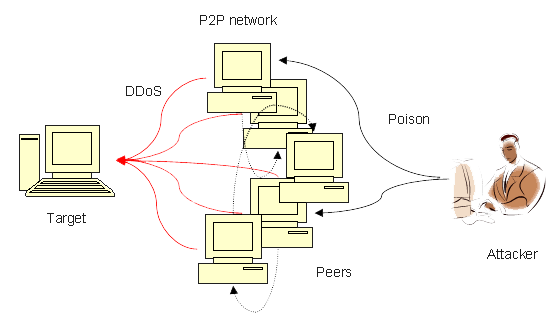
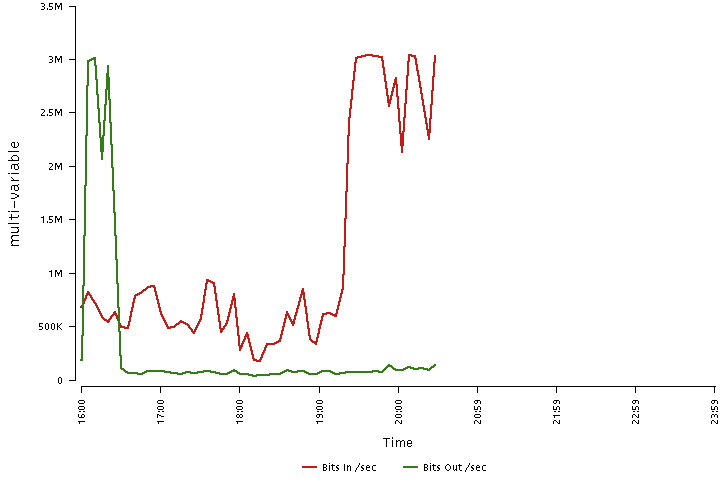
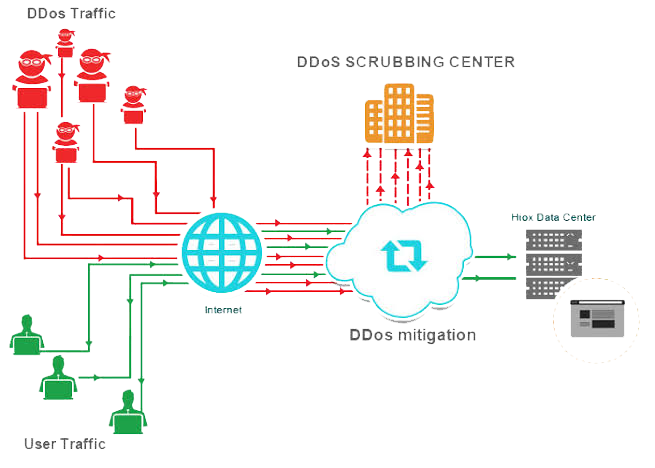
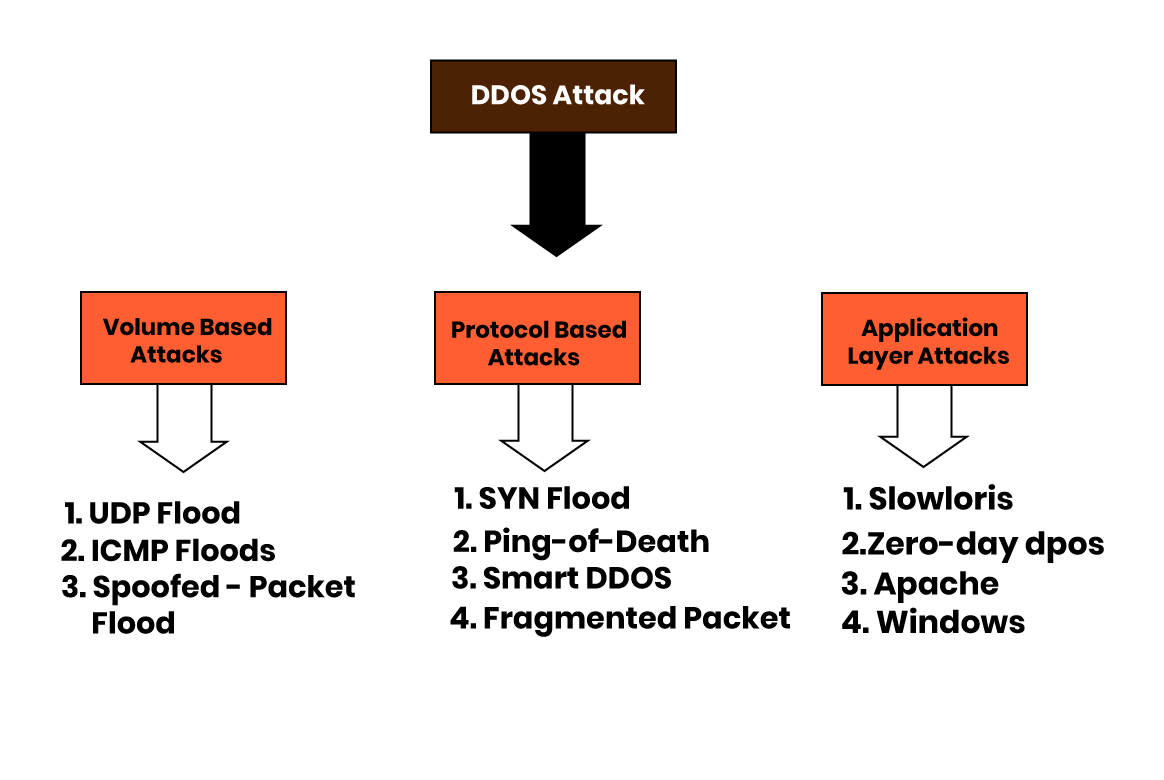 There is a rise in DDoS attacks in the past few years. and even the attacks are now getting stronger and more harmful. In such a scenario it becomes important to take mitigate these attacks to avoid any future security risks.
There is a rise in DDoS attacks in the past few years. and even the attacks are now getting stronger and more harmful. In such a scenario it becomes important to take mitigate these attacks to avoid any future security risks.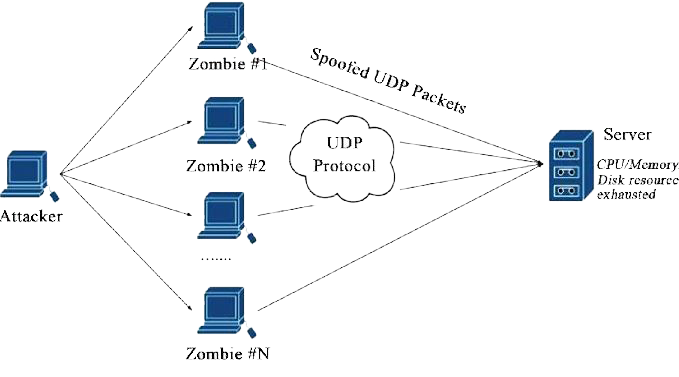
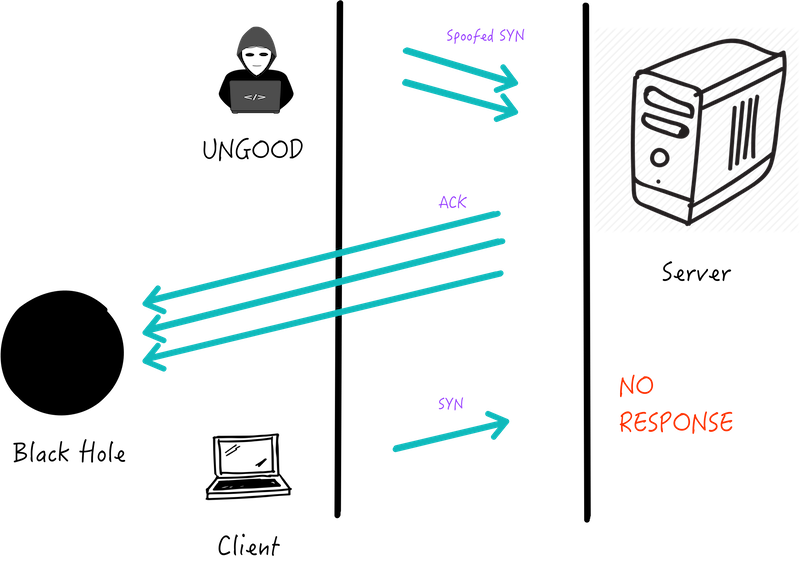
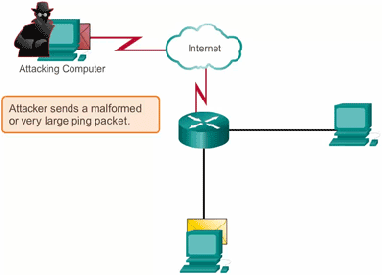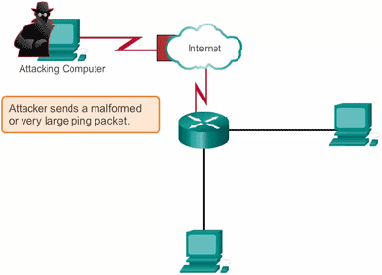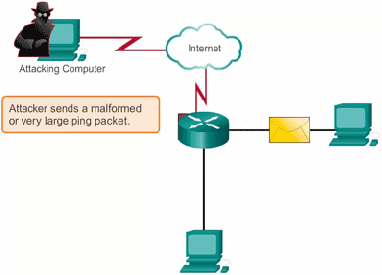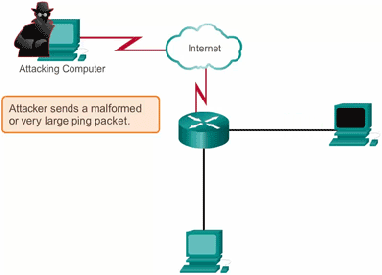


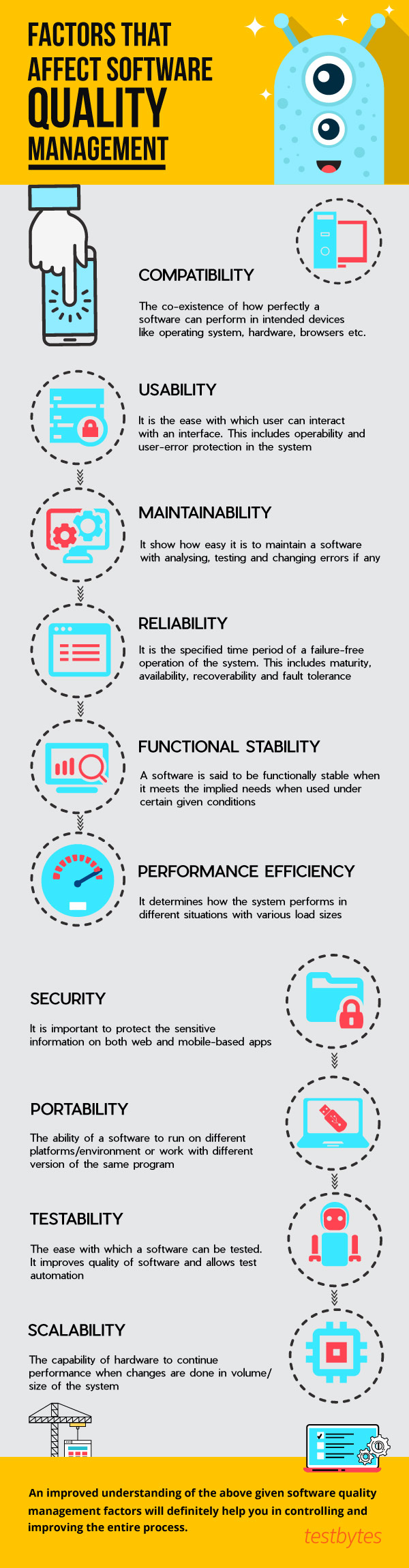
![10 Factors That Affect Software Quality Management [Infographic]](https://wp.testbytes.net/wp-content/uploads/2017/06/featured-image-Factors-that-Affect-Software-Quality-Management-2.jpg)