People, hold on to your hats! We’re entering the tumultuous world of data breaches, where businesses quake like alarmed squirrels and chaos erupts at every turn.
This is not something to take lightly, I assure you. Imagine sensitive information about your company being made public, resulting in chaos and mayhem beyond anything you could have imagined. Yikes!
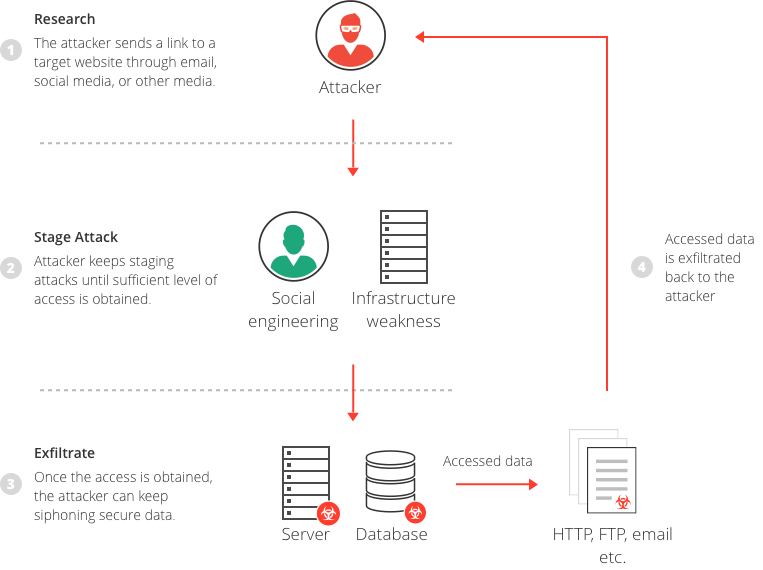
So, you ask, what precisely is a data breach? It resembles a cunning cat burglar breaking into the digital fortress of your company, stealing priceless information, and causing havoc in its wake.
There is more to this story, so hold on tight. We’ll examine the different types of breaches, including hacking, insider threats, and even actual physical intrusions on the order of a Hollywood heist. Wondering how these cunning attacks take place?
Here is all about data breaches in detail.
What is a Data Breach?
In simple terms, a data breach means the personal and confidential data of a person or an organization is made available in an untrusted environment by unauthorized people without the consent of the person or organization concerned. This is sometimes also called a data or information leak.
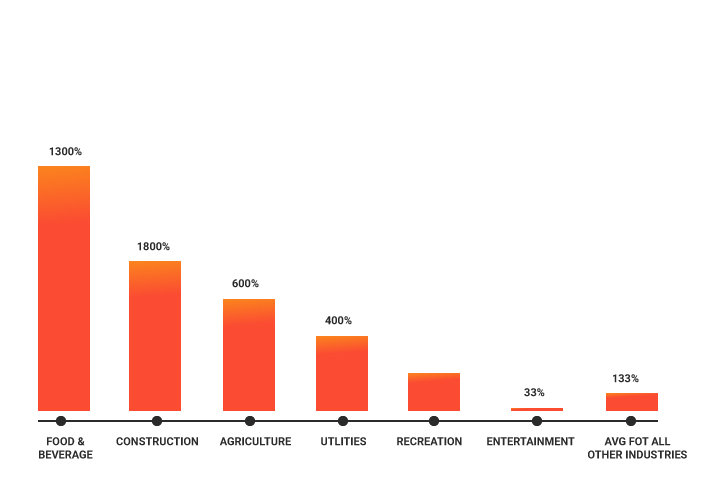
Data breaches can have legal consequences and hence closing the loopholes is becoming a big priority for all organizations.
It is important to understand that it is not external elements that are trying to access your data but there can be several other intentional and unintentional things happening within your company that can lead to a data breach.
Some of the major data breach stats for 2023
- 84% of code bases had at least one open source vulnerability, according to Synopsys researchers.
- Over six million data records were exposed globally during the first quarter of 2023 due to data breaches. Since the first quarter of 2020, the fourth quarter of 2020 saw the highest number of exposed data records, or nearly 125 million data sets.
- Cybercrime peaked up to 600% than the previous years in the covid pandemic time
- Small businesses are the target of 43% of cyberattacks, but only 14% of them are equipped to defend themselves, according to Accenture’s Cost of Cybercrime Study.
- Malware attack is the most common type and 92% of the attack is delivered through email
- By 2023, it is expected that the average cost of a ransomware attack will be $1.85 million per incident.
- The company Lookout claims that in 2022, when half of all mobile phone owners worldwide were exposed to phishing attacks every three months, the highest rate of mobile phishing ever recorded was seen.
- Concerningly, 45% of respondents admit that their security measures fall short of effectively containing attacks, and a startling 66% of respondents say they have recently been the victim of a cyberattack. Furthermore, a sizeable majority of 69% think that the nature of cyberattacks is changing and becoming more targeted. These figures demonstrate the urgent need for improved security protocols and preventative measures to deal with the growing danger of cyberattacks.
- 43% of c-suite business leaders reported data breaches on 2020
- So far, in 2021 phishing attacks climbed to 36% compared to 22% in 2020
Types of Data Breach
Based on how and where the data breach happens it can be classified into several types. Let us investigate these types now.
- Unintentional or internal errors by the Employees
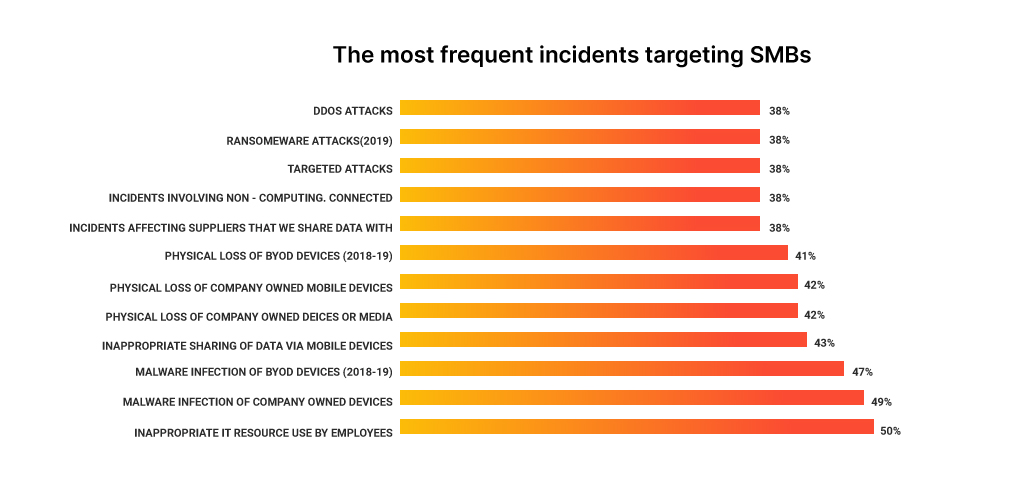
Employees are the biggest asset of any company. This asset can be the strongest and weakest link in the security chain. Sometimes they tend intentionally or unintendedly help in data breaches. Incidents like sending a bulk email with all the people in CC instead of BCC, or responding to phishing emails and compromising sensitive information, exposing sensitive information during screen sharing sessions with the people inside or outside the organization contribute to the data leakage to authorized people or environment.
Sometimes employees can be indirectly contributing to the data breach by not following the right security standards. Like not installing the proper system updates, using weak passwords or not securing the database with a password could make it easy for people from outside to access the company data.
- Cyber Attack
Cyber Attacks have become common these days. We frequently hear the militant groups defaced the govt websites. A more common word for it would be hacking. To put it in words a cyber attack means attacking a computer, network, or server with the intention of stealing information, alter and delete data causing intentional damage to the other organization.

The most common form of cyberattacks is using malware which captures the user’s sensitive information and uses this information to cause damage to him or his assets. Like at an individual level it can be used to gather a person’s bank login credentials and then used from transferring his money to other accounts. Some malware can help you get complete control over the other system, such that it can perform tasks under your command.
- Social Engineering

This is one of the most common forms of attack. Here the criminals and hackers pose as legitimate and authorized personnel and try to gather sensitive information from the company employees. One of the common methods used is phishing. This includes emails that look very real and people are tempted to open them or click links in them that will compromise the security.
This includes emails like password expiry with reset link or mandatory training list with a link to the training, courier received, and many more. The employees need to be vigilant and should report these kinds of emails to their security team to avoid further damage to the company and its data.
- Unauthorize Access
Inside the office premises, there are likely to be several important documents containing sensitive information. It is important thus for the organization to implement proper access controls. The rooms should be made accessible only to people who are authorized. The same goes for internal applications.
Read also: How to Secure Your Website From Hackers
For e.g. the personal data of the employee which would include his salary. This needs to be accessible only to HR, his manager, and himself. If another person can access this data, then that will also be called a data breach even though the information may not be transmitted outside the organization.
- Ransomware
This is one of the fastest-growing cybersecurity threats across the globe. This type of malware will encrypt all the files in your system. Without the decryption key, you could end up losing all your data. At this point, the attacker can blackmail the organizations for huge amounts for sharing the decryption key.
This is a very serious threat for almost all organizations because even with all the network security in place this malware can easily make its way into your systems through phishing emails, attachments, etc.
The only way out is to take a frequent backup of your system and as soon the malware is detected you should clean your system and restore it with the last backup data.
- Intentional Damage
Employees can cause maximum damage to the organization since they have access to the data and information. In several cases, the employees would intentionally leak the data to unauthorized people outside the organization for monetary gains or take revenge.
There is no way no control these kinds of data breaches apart from educating the employees against doing it and setting up a structure where other employees can anonymously report any suspicious activity by the others.
- Theft
The systems in an organization contain a lot of information. Physical theft is another contributor to a data breach. This includes the computers, hard disks, and even the hard copy of documents that are not shredded after use.
Theft not necessarily means someone breaking into the office it could also occur outside the organization. Like an employee in a coffee shop with his laptop unattended, or an important document left in the dustbin without shredding can make its way to landfills and fall into unscrupulous hands while disposing of laptops and other digital media if data is not completely erased it can also lead to a data breach.
Read also: What is a DDoS attack? How to Stop DDoS Attacks?
These data breaches are prevalent across all sectors. Banking and Healthcare are the most critical among them. When it comes to healthcare the picture is sad. The medical data, reports, and billing details are sold in black.
This data is then used to manipulate the patients into buying more costly medicines, higher premiums for insurance, and many other shady activities. It is a big business. Make sure when you visit a hospital or medical center, they have proper data protection measures in place to avoid such situations.
How does Data Breach Occur?
A data breach is so easy to carry out at this juncture of time. But what are the reasons that make data breach too easy to carry out or how does data breach occur?
- Weak and stolen credentials
- Applications that are built based on poorly written code
- Poorly designed network
- Malicious link and software
- Over permissions
- Companies inside the companies
- Improper configuration
How to Prevent a Data Breach?
Now that we have seen how a data breach can happen and what can be the consequences, let us try to fix the damage. While it may not be possible to make the system 100% foolproof, below are some of the ways in which each organization can try to minimize the occurrences of these data breaches.
#1) Keep only what you need
Extra data and information storage can become cumbersome to manage and maintain. The best way is to store only the necessary information both as hard copy and soft copy. Another way is to educate the employees about the retention period of different categories of documents as per the business needs. It is also important where you keep your data. Always make sure not to store important data in multiple places. 1 backup should be enough.
#2) Secure Your Data
As simple as it may sound, having proper safety controls in place is very important for Data Loss Prevention (DLP). Ensure the rooms have limited and restricted access. Ensure not to provide temporary access to anyone for these rooms. Also, regularly revisit the access controls to ensure that only required people have access and ensure to remove access for people who no longer need it
#3) Educate the employees
Employees are your best bet against a data breach. It is advisable to create extensive security policies to avoid data breaches and educate them about it as well. They should be told to follow the policies and security standards mentioned. The onus is on the company to make sure the employees are aware of these policies and standards to be followed.
#4) Destroy before disposing
Companies tend to dispose of unused and expired electronic data, including laptops and pen drives. It is important that the data in these electronic devices is destroyed before it is disposed of. This would help avoid the threat of data getting into the wrong hands after disposal.
#6) Update your policies
With new means of a data breach and information leak being identified, one must make sure that the security policy of the company is updated regularly to counter such attacks. The employees should be notified and made to understand the policy updates made from time to time to make sure they are vigilant against phishing attacks and potential data breaches.
#7) Enhance digital security
Digital security needs to be enhanced with the use of strong passwords containing mixed alphabets and numerals, the encryption and decryption keys need to be changed regularly, and the digital data transfers need to be monitored especially the information shared outside the intranet.
#8) Keep software and system updated
Keeping the system and software updated is always your best bet against malicious malware attacks. While hackers are trying new ways to break through into your system, the security and anti-virus companies are always trying to block these attempts. It is thus important to make sure that all systems install these important updates.
#9) Password Guessing
Password Guessing is one of the most common ways to get unauthorized access into any system. Announcing your password in public and writing it randomly on a slip or a whiteboard can reveal your password to a large number of people apart from the people you want to get access to it. Hence leading unwanted people to get access to your system.
Another very common flaw is keeping the password weak or guessable. Many people keep their passwords on their birthdays, street names, pet names, etc. that are easily guessable by other people. This can also lead to hackers getting access to your system and exploiting it.
Your password is like a key to your home, if it reaches the wrong hands, your valuables can be stolen. Similarly, if you lose your password to the wrong people, you have a chance of getting your sensitive information stolen.
Always keep a strong password and ensure it’s secrecy.
#10) Recording Key Strokes
Recording Key Strokes can be done easily through malware called keyloggers. These keyloggers can record everything that is typed on your system. Everything including your emails, passwords, messages, credit card information, etc. This information can be then used by hackers to exploit your security.
#11) Insider threat
Sometimes your own employees can be a threat to you. They have your insider information, which they can reveal to your opponents. This again can be a blow to your data security.
Always be sure which information is to be passed to which employee and train them properly and get the proper documents signed to keep your security information safe.
#12) Eavesdrop Attack
An eavesdropping attack as a name suggests is like eavesdropping into someone’s private conversation. In digital words, in eavesdropping attacks, the hacker mimics themselves as a trusted server. This attack can be either
- An active attack
- A passive attack
In an active attack, the hacker who is mimicking as trusted serves sends queries to the victim and gets all the details from the victim, faking himself as a trusted source.
In a passive attack, the hacker listens or eavesdrops on the information being transferred on the network.
#13) Data Backup and Recovery
Data recovery and backup are essential for reducing the effects of a data breach. Having reliable data backup and recovery mechanisms in place can help organizations recover their compromised data and minimize the damage in the event of a breach, where unauthorized access or data loss occurs.
Organizations can guarantee that they have a secure copy of their data stored apart from the production environment by routinely backing up important data and systems.
This enables them to fix the underlying security problems before restoring the data to its pre-breach state or a known clean state. Additionally, data backup makes it easier for forensic investigations to determine the reason for and scope of the breach, supporting incident response efforts.
Data recovery from backups also lessens the chance that ransomware attacks will be successful because businesses can restore data without having to pay the ransom. A company’s resilience is increased by the implementation of effective data backup and recovery procedures, which guarantee that crucial data is accessible even in the event of a data breach.
Risk Mitigation Strategy
- Create an incident response plan that is clearly defined and frequently updated to serve as a roadmap for action when a breach occurs.
- Conduct frequent risk assessments to find any potential holes or flaws in your systems, networks, and data handling procedures.
- Assign data a level of sensitivity and put the right security measures in place to protect high-risk data first.
- Apply the least privilege principle to make sure that people only have access to the information and systems they need to carry out their specific roles.
- Put in place reliable monitoring techniques to spot irregular behavior or potential security breaches and act quickly.
- Evaluate the security procedures followed by partners and third-party vendors who handle sensitive data, and establish strong legal contracts to guard against data breaches.
- Educate staff members on security best practices and how to spot and report security threats by conducting regular security awareness training sessions.
- Use encryption methods to protect sensitive data while it is in storage or being transferred, lowering the possibility of unauthorized access in the event of a breach.
- Applying security patches on a regular basis will address known flaws in software, systems, and equipment.
- Network segmentation limits an attacker’s ability to move laterally in the event of a breach, potentially reducing damage.
- Implement thorough logging and monitoring systems to record and examine security events, assisting with breach detection and investigation.
- Conduct periodic security audits to evaluate the efficacy of security controls, spot any gaps, and make the necessary corrections.
- Consider purchasing cyber insurance coverage to lessen financial losses and legal obligations brought on by data breaches.
Some of the Biggest Data Breach Incidents
Even with the policies and procedures in place, companies do fail to protect their data and personal information. These data breaches can have far-reaching consequences if not found and plugged at the right time. In this section, let us see some major and most talked about data breach instances across the globe.
In September 2018, the hackers were able to manipulate the code for “view as” to get access to the user security token. With this token, it was possible to hack into the person’s Facebook profile. This exposed the personal data of 50 million users. To counter this Facebook had to forcefully log out 90 million users and had to reset the access tokens as well.
- British Airways
In a major data breach that happened in 2018, the hackers were able to access the British Airways customer database and get the personal and financial details of more than 3,80,000 customers who made or changed any of their bookings over a 2-week period. The compromised data included name, address, email ID, credit card details including the expiry, and some security codes as well. Even before they could fix the damage, another 1,85,000 customers’ data were compromised through the reward bookings vulnerability.
- American Medical Collection Agency (AMCA)
AMCA is a billing service agency in the US. Their medical data was breached for about 8 months from Aug 2018 to Mar 2019 before coming to light. Though the investigations are still, a rough estimate indicates that personal, medical and financial data of more than 25 million people was compromised. The extent of the impact is still under investigation and the company has recently filed for bankruptcy.
- Equifax
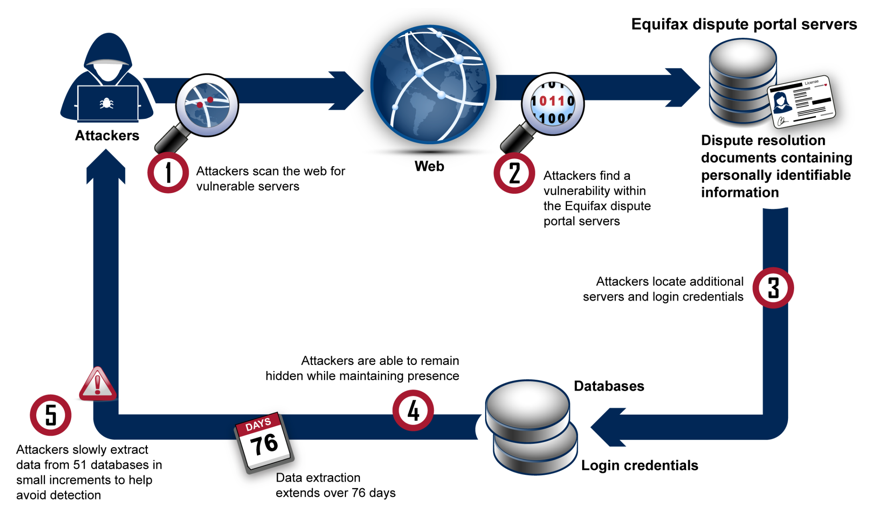
One of the US’ biggest credit reporting companies faced the wrath of hackers in 2017 jeopardizing the data of more than 143 million users who had used their services for generating a credit report. The breach took about 2 months to find and fix and the hackers were able to get the SSN, DOB, names, address, and even driving license details. As a precautionary measure, the clients were asked to freeze their credit cards or at least enable a fraud alert. The exact extent of the impact is still unknown.
- Oregon Department of Human Services
This was a result of a massive phishing email campaign to which around 9 employees responded by providing their user IDs and password. With this information, the hackers were able to gain full access to the medical data and records of about 6,45,000 patients. This included their personal record, financial data, medical history, and SSN details as well. The officials were detected the data breach 3 weeks later when most of the damage was already done.
- eBay
In one of the biggest corporate data breaches in history, the hackers were able to access and compromise around 145 million customer data including the username and password. The company for initially reluctant to believe a data breach in its high-security system. But later, they found that the hackers had used the corporate accounts of three employees to access the customer data. The customers were then asked to reset and update their passwords to avoid any unforeseen issues.
- Community Health Systems
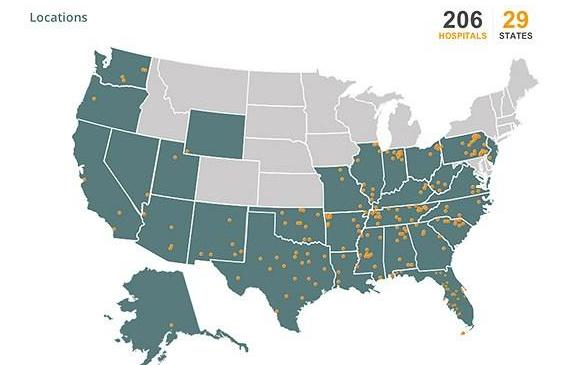
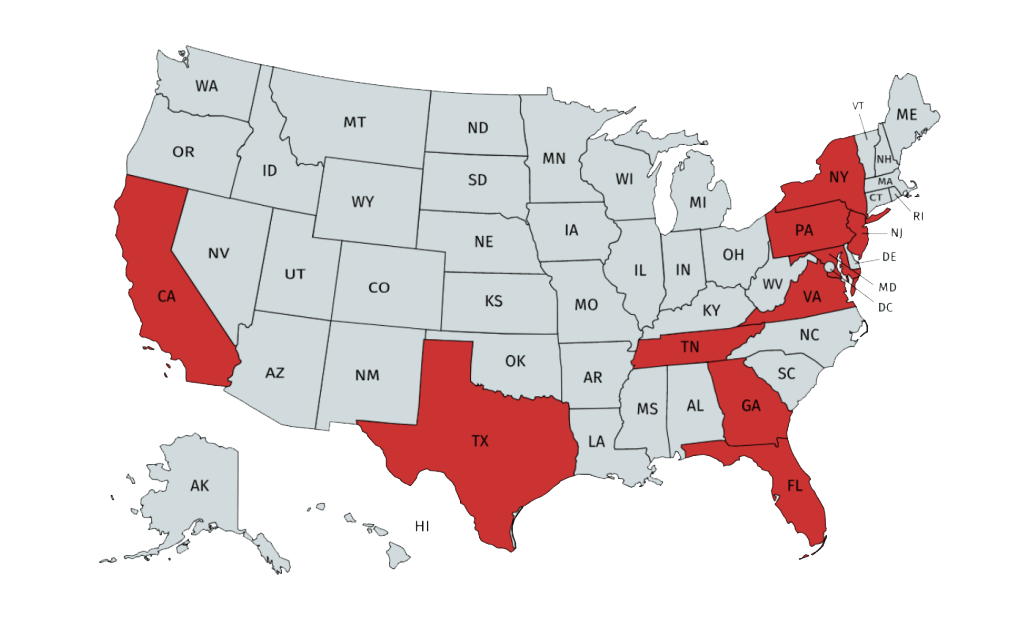
Around 206 hospitals in the US come under the umbrella of the Community Health System. In a major data breach in 2014, the hackers were able to access to more than 4.5 million patient records belonging to these 206 hospitals.
Read also: Top 10 Most Common Types of Cyber Attacks
This indicated a very high risk of identity theft of the patients belonging to Texas, Tennessee, Florida, Alabama, Oklahoma, Pennsylvania, and Mississippi where they have most centers. They were later able to find out that the data breach was carried out through sophisticated malware by hackers from China.
Ways to improve Data Breach Mitigation
- Companies have deployed an incident response team to respond timely when there is an attack so that days required data breach cycle can be reduced.
- The incident response team should be tested using a mock drill to ensure its reliability.
- The latest technologies must be implemented to detect the breach at an early stage.
- For better insights and to stabilize the security seek the help of threat intelligence
- Have an effective business continuity plan and proper backup
Seek expert advice rather than listening to half-witted one
How Much Does Data Breach Mitigation Cost
The average cost of data breaches globally according to a study in 2019 is $3.92 million. What makes such attacks devastating is that the time is taken to find the attack and stop it.
One data breach cycle is 279 days and often companies find it hard to contain the attack before it. However, there are companies that have managed to put an end to the cycle before 200 days managed to reduce to the loss of $1.2 million less than the usual.
The most devastating attacks were caused by malicious attackers and it took longer than the usual average to detect such attacks. For example, you have the case of Wiper Ransomware attacks in front of you.
Conclusion
While data breaches have become common and even the biggest companies are not spared by them, we must make sure we take all precautions to keep our data safe and secure.

It is important to understand that with greater connectivity all data is at stake both for individuals and for companies. This means that even as an individual you need to understand the importance and of your personal information and you need to safeguard it against misuse.
