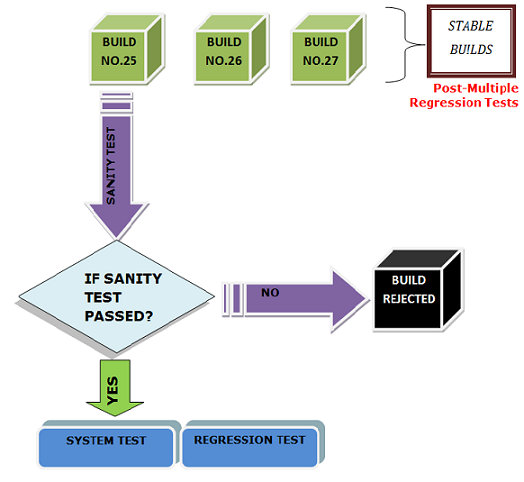
Security testing is a technique that aims to determine if a system or software performs well enough to protect data and deliver functionality as planned. This technique forms to be an integral part, when it is considered in terms of testing software for banking, website hosting or any other high-security application.
It works on six basic principles that include confidentiality, integrity, authorization, authentication, non-repudiation, and availability. Performing this technique is a challenging task as it requires a tester who has in-depth knowledge and understanding of the process so that he/she is able to check and verify any risk factors, loopholes or issues in the program.
As compared to the normal testing, this method aims to break the entire program into different parts and then, test its safety and security under normal and abnormal circumstances.
With a large number of software and apps available in the market, there is certainly an increasing demand for high performing and reliable security testing tools that can help ensure that these programs are up to the mark in terms of their security.
While there are several companies that offer a number of high performing security testing tools to the market, these 15 top the chart of the most powerful and reliable security testing tools.
Popularly used for penetration testing, Metaspoilt is one of the most advanced frameworks that work on the concept of ‘exploit’. Exploit is a code that can test a system to extremes by surpassing the security measures and entering the system. When entered, exploit runs a ‘payload’, which is a code that performs operations on a target machine, to create the most appropriate framework for penetration testing.
This framework can be used for security testing on web applications, networks as well as servers.
Available for free, Wireshark is one of the most popular open source packet analyzers. This protocol is capable of providing the users with the minutest details about the network protocols, packet information, decryption, and others. One can use this protocol on Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and many other systems.
W3af is a freely-available web application audit framework that works effectively against multiple odd vulnerabilities. With a GUI that is available with expert tools, this framework is capable of sending HTTP request and cluster HTTP responses. Some of its impressive features include quick HTTP requests, integration of web and proxy servers into the code, etc.
This tool can be used for multiple testing purposes such as, mobile device penetration, password identification and cracking, network device penetration, and several others. With a GUI click-able interface, this works best on Microsoft Windows and is one of the most expensive tool in this category.
Available with a vigorous web application scanner, Netsparker is an excellent tool to recognize vulnerabilities and accordingly suggest remedial action. Available with a command-line and GUI interface, Netsparker can help on to exploit SQL injection and LFI (local file induction).
This is one such tool on which security testing specialists highly rely. Although this tool majorly functions as a scanner, Burpsuite has a limited scope to deal with attacks. Interrupting proxy, creeping content and functionality and web application scanning are some of the common functions performed by this tool.
Cain &Abel is an excellent tool to crack encrypted passwords and network keys. Available exclusively for Microsoft operating systems, the functions are performed on the basis of network sniffing, Dictionary, Cryptanalysis attacks and Brute-Force and routing protocol analysis methods to achieve this.
Developed specifically for web applications, acunetix is a scanner that helps identify the probable dangers for these applications. This security testing tool performs various functions for its users such as SQL injection, cross site scripting testing, PCI compliance reports etc. Although a bit expensive, one can get its free trial version to understand how it actually works.
Available as a complete package known as Retina Community, this is one such tool that targets the entire company at once. The Retina is a commercial product that should be used more as a vulnerability management tool instead of a pen-testing tool.
Canvas is a security testing tool that can be used for testing the security issues of web applications, wireless systems, and networks. With multiple payload options, this tool is available with GUI interface and can work on Linux, Apple Mac OS X, and Microsoft Windows.
Also known as Network Mapper, this tool is a must have for ethical hackers as it makes it easy to understand the characteristics of any target network. These characteristics can include things like host, services, OS and packet filters. The tool is open sourced and can perform in any environment.
This tool is an open source framework, which is used majorly for keeping a record of information that can be shared among multiple participants of penetration testing. When this information is interpreted, it helps them understand the details of testing such as, the aspects that are already covered and others that are still to be covered. With a GUI interface, this tool is open source and can work on Linux, Microsoft Windows and Apple Mac OS X.
Security is an easy to manage security monitoring system that can be used in place of expensive commercial grey boxes. Simple to setup and configure, this tool is an effective way to identify any security related issues on the network.
This is a web server testing tool that entered the market of security testing tools almost a decade ago. The tool is highly effective to identify vulnerable scripts, configuration mistakes and related security problems. However, this tool cannot identify XSS and SQL web application bugs.
Vega is a vulnerability scanning and testing tool that works well on various platforms including OS X, Linux and Windows platforms. With a GUI, Vega is available with an automated scanner and an interrupting proxy that can help identify web application vulnerabilities, header injection, cross site scripting etc.
Apart from these, there are a number of other security testing tools already available in the market or ready to be launched with latest upgrades. The ultimate purpose of using any such tool is to deliver an exclusive product that ensures the maximum benefit to the company.