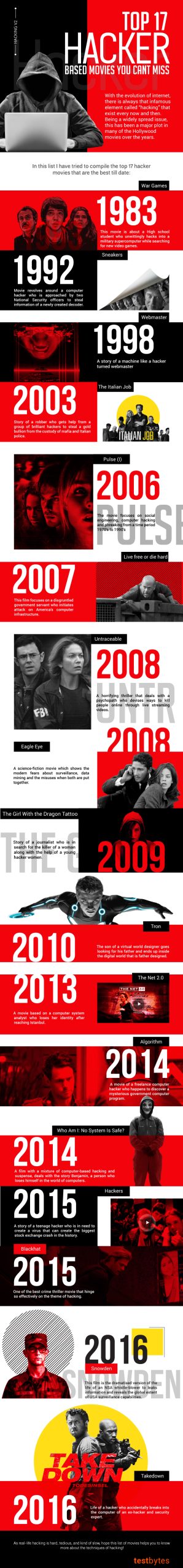
The Internet of Things (IoT) is a network or system of physical objects such as vehicles, devices, and buildings that are embedded using electronic devices, software or microchips. Designed with an aim to collect and exchange data of a different type, the technology gives the user an ability to control devices even from a far-off place over a network.
The real-life implementation of this technology can be seen in wearable gadgets such as Fitbit bands, applications to collect the real-time outdoor lighting data, healthcare devices, etc. Some of the common reasons for an increasing number of organizations adopting this technology are optimization of operations, reduced cost and improved efficiency.
IoT Testing
IoT Testing has become a crucial element to ensure the effective functioning of all the devices and technology that are being used in its environment. To conduct this form of testing, it is important for the QA team to design an effective and comprehensive strategy that allows them to test and cover all the dimensions of the IoT testing. This strategy would include everything from the types of testing, tools for testing, test lab setup, etc. To avoid all sort of hiccups, the team can also plan in advance about the methods to be used for evaluating data simulation and virtualization.
Even while the team might prepare itself well in advance to conduct this form of testing, there are a number of complexities that they might have to deal with. Some of them are mentioned below:
1. Multiple IoT platforms
An individual IoT device works on its own software and hardware. It also integrates with an application software to issue commands to the device and examine data gathered by the device. This, in turn, leads to multiple combinations of hardware and software devices that are required to be tested to ensure a smooth functioning of all the devices.
It is, therefore, important to gather relevant information from the users and develop some easy subsets to be tested. This would allow the testing team to analyze all possible combinations that are generally in use by the team.
2. Numerous IoT communications protocols
A number of different communications protocols are used by the IoT devices to communicate with the controllers and with each other. Some of the common ones used are Message Queuing Telemetry Transport (MQTT), Extensible Messaging and Presence Protocol (XMPP) and Constrained Application Protocol (CoAP). Available with their own set of advantages and disadvantages, MQTT is the most popular for its high potential and performance.
The transport layer is often layered with an API, which is generally based on JavaScript Object Notation (JSON) or XML. These protocols and APIs are used by the testers to conduct automated testing using a testing design and tools that support these protocols and API s.
3. Higher number of attack surfaces and other security threats
Since more than 70 per cent of the IoT devices is vulnerable to develop security issues, it is important to keep a tab on such issues and fix the same. When conducting the tests, it is important for the testers to be very particular about the device’s password policy so as to ensure that these are fulfilled and the minimum requirements are fulfilled.
The best way to stay secure is to set up a mandatory password change upon its first access. This is required to be considered when the team is developing automated tests for the device.
4. Diversity in IoT apps and devices
The huge varietyofIoT apps and devices demand high testing capabilities in the team. This is to ensure that all the aspects of these applications and devices are tested thoroughly to ensure that these also exceed the desired user expectations. To ensure this, it is required form the testing team to have a strong understanding of the testing processes, the device’s architecture, etc.
If there is some sort of dependency on third-party services and the same are unavailable due to some sort of reasons, it is still possible to run the tests by virtualizing the system and removing all sorts of dependencies on the third-party services.
5. Fast-moving data and increased load
Overloaded WiFi channels, defective network hardware, and slow or inconsistent Internet connections are some of the common issues that occur in connected IoT devices. In order to ensure the smooth functioning of the IoT devices, it is important to test all these devices under different situations and that they respond quickly without causing any sort of data loss.
IoT is the present and the future
The approach to conduct IoT testing varies from system to system but it is important for the testers to ensure that they keep their focus on Test-As-A-User (TAAS) instead of testing as per the requirements.
While the task might seem to be challenging and complicated to the team, but it, definitely, is interesting to test and ensure an optimum functioning network of devices, operation systems, firmware, and protocols. It is expected that in near future, the system will be defined in a much better way hence, reducing all sort of complexities involved in this job.



















![Top 17 Hacker Based Movies You Cant Miss [Infographic]](https://wp.testbytes.net/wp-content/uploads/2018/02/Top-17-Hacker-Based-Movies-You-Cant-Miss-featured-image-2.jpg)