Mobile apps become a double- edged sword especially when a mobile payment application has to do mass transfers. New features are prone to hacking and extortion if not handled with care. NowSecure Mobile Security Report 2016 has found that 25% of the mobile applications always deal with at-least one highly extended security risk. When attacks on mobile applications increased, authorities started considering security checks before launching the app.
Here, we are going to discuss about 7 possible security testing errors that may occur but can be avoided:
- Failing to understand how an application is exposed to risk
We know that to cure a disease, we have to understand the cause first. So, it’s necessary to analyse the possible security risks that can affect the user, device and systems, and the damages it can bring. ‘Threat modeling’ is a practice which helps organizations to analyse the potential of risk, measuring up the development and growth of the threat. Usually, the risks happen to be identity theft and financial fraud, where the password and user name to any kind of financial account of an individual is hacked. The type of attack depends on the hacker’s motive.
- Failing to connect security with application design
Usually, security testing is left to be done at the end of the development process or is never done at all. This is mainly due to the misconception among developers that security testing costs a lot. But, patching up the bugs after the application reaches the audience is more expensive than designing a security checked code from beginning.
- Lacking the quality in security testing
Checking vulnerabilities and block box testing should be included while performing security tests. Penetration testing has the ability to prevent bugs and malware from real world hackers and keeps apps secure. It is always better to arrange a professional security than an in- house testing team with little knowledge in security testing.
- Use end-end encryption in data
Using weak or no encrypted data is a commonly made mistake which make data theft easier for the hacker. To avoid malwares, it’s better to use the end-end encryption in data for all data transferred through mobile devices. Apart from that, it is also important to input the encryption feature in devices so that non transmitted data is also secured. This has to be built directly into the device.
- Exposing sensitive data
Try not to use password remembering feature which may lead to accidental login without the user being aware. Easy access to the login details can help hackers find the weakest points of an account. Never keep sensitive data unattended. Always ensure their safety. An experienced hacker may always try tricks on users to retrieve information.
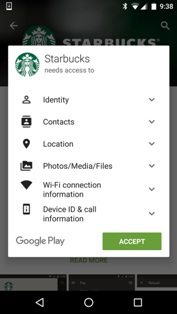
- Limit app features
Avoid adding features that doesn’t add value to your app. Keep the number of features to a minimum; it ensures that the app leaves a smaller surface for security attacks to happen, thus increasing safety. . THE same applies to permission requests, and therefore, ask permissions only for the necessary details.
- Develop a security response plan
A 100% secure application is not possible, even though it passes through every type of testing. Technology is growing fast that new vulnerabilities are also being made every day to beat security plans.
We just can’t do anything about it.
But!
A critical action plan can be implemented by:-
1. Monitoring the device, identifying every unusual activity
2. Appointing an in/out house team to identify and recover threats
3. Having policies that help you to limit the damages
